Cybersecurity Snapshot: Many Employees Overshare Work Info with AI Tools, Report Finds, as ‘Cybersecurity Awareness Month’ Kicks Off

Check out the best practices cyber agencies are promoting during Cybersecurity Awareness Month, as a report warns that staffers are feeding confidential info to AI tools. Meanwhile, a study highlights how business decisions can derail OT security. Plus, get the latest on Active Directory security, CISO salary trends and ransomware attacks!
Dive into six things that are top of mind for the week ending Oct. 4.
1 - CISA to promote MFA, software updates, phishing protection during Cybersecurity Awareness Month
October has arrived, and with it Cybersecurity Awareness Month, now in its 21st year. This global effort aims to make people aware of cyberthreats and to share cybersecurity best practices.
In the U.S., the Cybersecurity and Infrastructure Security Agency (CISA) and the National Cybersecurity Alliance (NCA) are promoting their “Secure Our World” campaign. Specifically, they’re encouraging people to:
- Boost their password security by crafting strong passwords, which are long, random and unique, and by using a password manager to generate and store them.
- Protect all accounts that offer multifactor authentication (MFA) with this security method.
- Learn how to spot phishing attempts made via email, text or voice calls.
- Keep all your software updated.
“Our focus is working with government and industry to raise cybersecurity awareness and help everyone, from individuals to businesses to all levels of government, stay safe online in our ever-connected world,” CISA Director Jen Easterly said in a statement.
As an official Champion of the CISA and NCA Cybersecurity Awareness Month effort, Tenable is committed to reducing risk, raising awareness and staying alert to the daily actions that help protect the world against cyberattacks.

Meanwhile, in the European Union, the EU Agency for Cybersecurity (ENISA) is focusing its awareness campaign on social engineering scams, such as phising and vishing.
“This threat category encompasses a wide range of activities that attackers deploy when attempting to gain access to either information or services through exploiting human error or behaviour,” reads an ENISA statement.
To get more details, check out:
- CISA’s announcement “CISA Kicks Off 21st Anniversary of Cybersecurity Awareness Month”
- The “Secure Our World” campaign toolkit
- This infographic from the Center for Internet Security
- The Cloud Security Alliance’s Cybersecurity Awareness Month landing page
- This video from CISA Director Jen Easterly
2 - Cybersecurity Awareness Month report: AI oversharing is out of control
Almost 40% of employees have fed sensitive work information to artificial intelligence (AI) tools without their employers’ knowledge, which highlights why organizations must urgently adopt AI usage policies and offer AI security training.
That’s one of many eye-opening findings in “Oh, Behave! The Annual Cybersecurity Attitudes and Behaviors Report 2024-2025,” published by the NCA as part of Cybersecurity Awareness Month.
Organizations must understand that employees inevitably will use generative AI, the report says, because of the productivity boost it offers; and that employees need guidance to understand the risks of using this technology.
Have you ever shared sensitive work information without your employer’s knowledge?
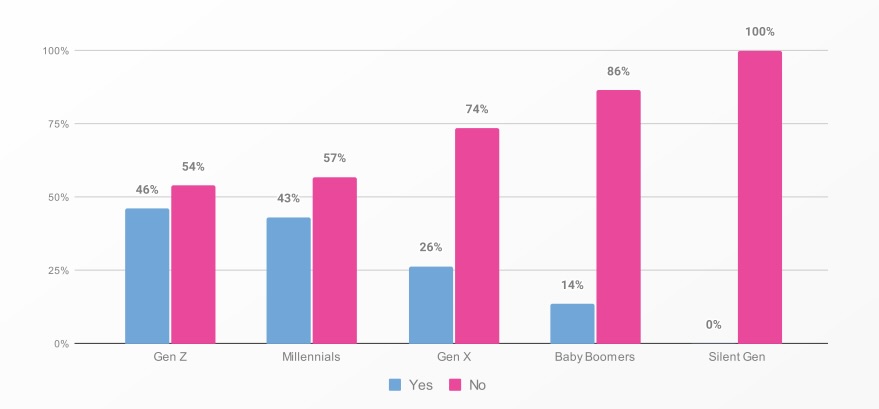
(Source: “Oh, Behave! The Annual Cybersecurity Attitudes and Behaviors Report 2024-2025” study by the National Cybersecurity Alliance, September 2024)
For example, more than half of employees surveyed (52%) said they hadn’t received any training on safe usage of AI.
“AI is here. You need watertight AI governance, and you need it yesterday,” reads the report, now in its fourth year and based on a survey of about 7,000 people ages 18 and up from Australia, Canada, Germany, India, New Zealand, the U.K. and the U.S..
Other key findings from the 139-page report include:
- 65% of respondents are concerned about AI-related cybercrime
- 54% find it easy to stay secure online
- 35% were victims of cybercrime, with phishing the most common attack, accounting for 44% of incidents
- 56% lack access to cybersecurity training
- 65% consistently use unique passwords
To get more details, check out:
- The report’s announcement “Study: Less Than Half of AI Users Trained on Security and Privacy Risks”
- The full report
- This video
3 - Boosting critical infrastructure’s OT cybersecurity
How do business decisions impact the cybersecurity of operational technology (OT) systems in critical infrastructure organizations? That’s the key question tackled by a new guide authored by the Australian Cyber Security Centre (ACSC) in collaboration with cyber agencies from multiple other countries.
TItled “Principles of operational technology cyber security,” the document starts from the premise that it’s often difficult to determine how business decisions affect OT cybersecurity. Why? OT is extensively integrated into critical infrastructure organizations’ complex tech environments.

The 14-page document, published this week, aims to help critical infrastructure organizations “make decisions for designing, implementing, and managing OT environments to ensure they are both safe and secure, as well as enable business continuity for critical services.”
Specifically, “Principles of operational technology cyber security” outlines these six key principles for creating and maintaining a secure OT environment in critical infrastructure organizations:
- Safety is critical in physical environments because security breaches may result in life-threatening situations.
- It’s crucial for critical infrastructure organizations to have a deep understanding of their business, including which systems are vital for providing services.
- Because OT environments don’t change frequently, it’s paramount to protect data about system configurations.
- OT networks should be segregated from all other networks, including the internet and IT networks.
- It's key to protect the equipment and software supply chain of the OT environment.
- The OT security staff should receive the appropriate tools and training they need.
To get more details, read:
- CISA’s alert about the guide
- ACSC’s announcement
- The full “Principles of operational technology cyber security” guide
For more information about OT security, check out these Tenable resources:
- “Blackbox to blueprint: The security leader’s guidebook to managing OT and IT risk” (white paper)
- “How to Unlock Advanced IoT Visibility for Cyber-Physical Systems” (blog)
- “Unlock Advanced IoT Visibility in your OT Environment Security” (on-demand webinar)
- “Critical Infrastructure Cybersecurity: Disrupt OT Attack Vectors in the New Era of Distrust” (white paper)
- “CISA Finding: 90% of Initial Access to Critical Infrastructure Is Gained Via Identity Compromise. What Can You Do About It?” (blog)
4 - How to defend Active Directory against cyberattacks
Looking to boost your Active Directory defenses? Check out a new guide that details common AD attack techniques and offers recommended mitigations.
Published by cyber agencies from the Five Eyes countries – Australia, Canada, New Zealand, the U.K. and the U.S. – the guide “Detecting and Mitigating Active Directory Compromises” highlights critical AD weaknesses, including “permissive” default settings; complex relationships and permissions; and support for legacy protocols.
It explains how to detect and defend against 17 popular AD compromises, such as:
- Kerberoasting
- Unconstrained delegation
- Golden certificate
- One-way domain trust bypass
- Security identifier history compromise
“By implementing the recommendations in this guidance, organisations can significantly improve their Active Directory security, and therefore their overall network security, to prevent intrusions by malicious actors,” the 68-page document reads.
Overview of Kerberoasting
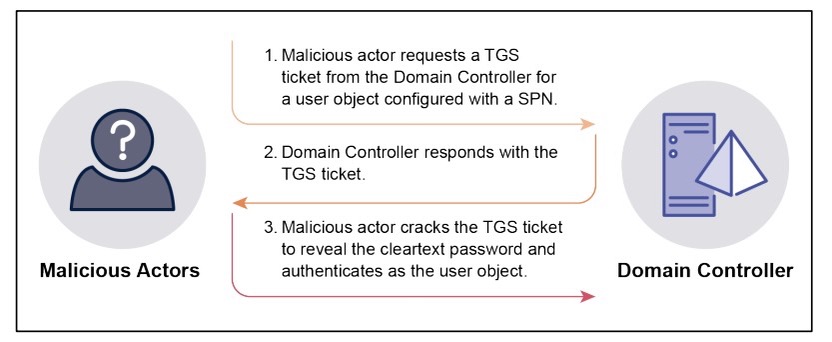
(Source: Australian Cyber Security Centre, September 2024)
For more information about securing Active Directory, check out these Tenable resources:
- “Identity has breached the ecosystem” (white paper)
- “Strengthen the Effectiveness of Your Identity Security Program with Zero Trust Maturity” (on-demand webinar)
- “Poor Identity Hygiene at Root of Nation-State Attack Against Microsoft” (blog)
- “Unveiling vulnerabilities in Active Directory: How the cloud exposes a 24-year old technology to attacks” (on-demand webinar)
- “Active Directory Master Class: Think Like an Attacker, Defend Like a Pro” (on-demand webinar)
5 - Survey: CISO churn rate drops again, as compensation grows 6%-plus
Back in 2022, more than one-fifth of CISOs changed jobs. Today, the story looks very different, as job turnover rates for CISOs have dropped significantly. As a result, most salary increases are coming in the form of relatively modest merit raises.
That’s according to the “2024 CISO Compensation Benchmark Summary Report,” published this week by IANS Research and Artico Search, and based on a survey of 755 CISOs, most of them (91%) based in the U.S.
While 17% and 21% of surveyed CISOs went to work for a new company in 2021 and 2022, respectively, those job-change rates fell to 12% in 2023 and to 11% in the first half of this year.
With less turnover than in the past two to three years, the majority of CISOs (70%) have gotten annual merit-based raises – a an average salary increase of 5.6%, and an overall average compensation bump of 6.3%.
“People have asked about salary depression in the security function but we see no evidence of it,” Steve Martano, an IANS faculty member and Artico Search cyber practice partner, said in a blog post.
Naturally, the ways to significantly boost your compensation are to either switch to a higher-paying job, or to receive a counteroffer or retention incentive from your current employer. Surveyed CISOs who went either of those routes got an average compensation boost of 31%. However, they were in the minority.
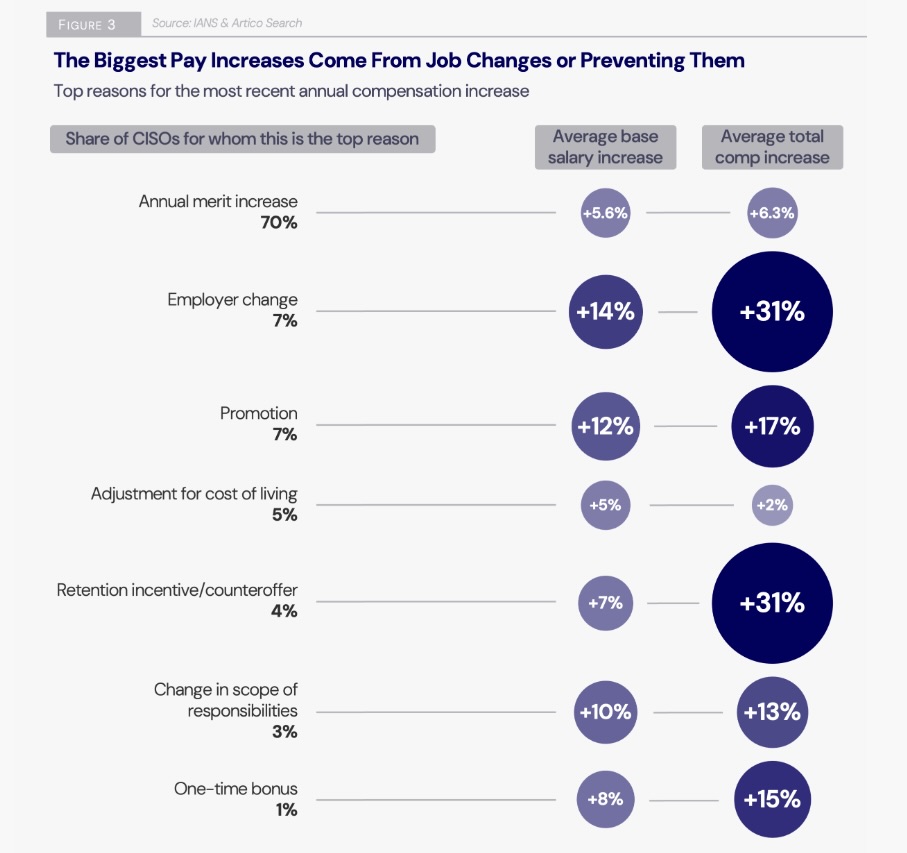
For more information about CISO trends:
- “What’s important to CISOs in 2024” (PwC)
- “5 CISO trends to keep up with during July of 2024” (Cybertalk)
- “2024 Deloitte-NASCIO Cybersecurity Study” (Deloitte)
- “The CISO’s Tightrope: Balancing Security, Business, and Legal Risks in 2024” (The National CIO Review)
- “State of CISO Leadership: 2024” (SC Media)
6 - Report: Ransomware attacks jump in August
Ransomware gangs turned up the heat in August, unleashing 14% percent more attacks than in July. The industrials sector was the hardest hit, receiving almost one-fourth of all attacks, another sign of ransomware groups' strong interest in attacking critical infrastructure organizations.
That’s according to the NCC Group’s “Monthly Threat Pulse: Review of August 2024” report, which found that ransomware attacks rose year-on-year as well – up 16% compared with August 2023.
“The increase in ransomware attack figures this month is demonstrative of the continuing volatility of the threat landscape,” Matt Hull, Head of Threat Intelligence at NCC Group, said in a statement.
RansomHub ranked as the most active ransomware group, accounting for 16% of all attacks observed in August. This ransomware gang increased its number of attacks by 67% compared with July.
Ransomware Attacks by Threat Actors
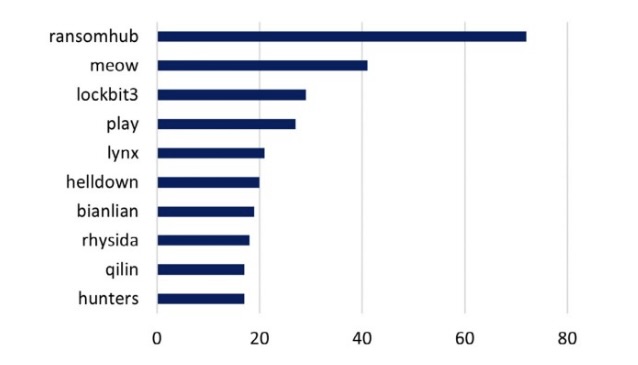
(Source: NCC Group’s “Monthly Threat Pulse: Review of August 2024” report)
- Cloud
- Industrial Control Systems Monitoring
- IT/OT
- Risk-based Vulnerability Management
- Cloud
- Cybersecurity Snapshot
- Federal
- Government
- Internet of Things
- OT Security

