Cybersecurity Snapshot: OpenSSF Unveils Framework for Securing Open Source Projects, While IT-ISAC Says AI Makes Ransomware Stealthier

Check out a new framework for better securing open source projects. Plus, learn how AI is making ransomware harder to detect and mitigate. In addition, find out the responsible AI challenges orgs face today. And get the latest on AI tool sprawl; ransomware trends; and much more!
Dive into six things that are top of mind for the week ending Feb. 28.
1 - New cybersecurity framework for open source projects
Here’s the latest industry effort aimed at boosting open-source software security.
The Open Source Security Foundation (OpenSSF) has crafted a new framework designed to offer cybersecurity guidance to leaders of open-source software projects.
The Open Source Project Security Baseline (OSPS Baseline), announced this week, is structured as a tiered set of security best practices and requirements drawn from established cyber frameworks, standards and regulations.
“It compiles existing guidance from OpenSSF and other expert groups, outlining tasks, processes, artifacts, and configurations that enhance software development and consumption security,” reads an OpenSSF statement.

OpenSSF created the OSPS Baseline after concluding that open-source project leaders often need help with cybersecurity. Meanwhile, users often lack visibility into whether and how an open-source software product was securely designed and developed.
“By meeting this ‘baseline,’ a project signals that it has taken essential measures to reduce the risk of common vulnerabilities and improve overall trustworthiness of the project to its adopters and contributors,” reads the OSPS Baseline FAQ.
The OSPS Baseline security controls are divided into three levels. Here’s a small sample of the controls in Level 1.
- Users must complete multi-factor authentication (MFA) when accessing a sensitive resource in the project’s version control system.
- When a CI/CD pipeline accepts an input parameter, the parameter must be sanitized and validated before it’s used in the pipeline.
- While active, the version control system must not contain generated executable artifacts.
For more information about open source security:
- “Top 10 Risks for Open Source Software” (OWASP)
- “Study highlights challenges, priorities in securing open-source software” (SC World)
- “Top 10: Most Common Open-Source Vulnerabilities” (Infosecurity Europe)
- “Seven ways to secure open-source software” (SC World)
- “Memory-unsafe code runs rampant in critical open-source projects” (Cybersecurity Dive)
2 - IT-ISAC: AI is changing the ransomware landscape
Ransomware groups will deepen their use of artificial intelligence this year, a trend that will help increase the number, severity and impact of ransomware attacks.
That’s one of the main takeaways from IT-ISAC’s report “Exploring the Depths: Analysis of the 2024 Ransomware Landscape and Insights for 2025.”
By leveraging AI, ransomware groups make their attacks harder to detect, prevent and mitigate. These sophistcated AI attacks modify their behavior and tactics in real-time as they analyze victims’ environments and protections.
“The integration of AI in the development of ransomware presents a new level of evolution in cyber threats,” reads the report from IT-ISAC, which stands for Information Technology-Information Sharing and Analysis Center.
“With AI, ransomware will be able to adapt in real time and be far more effective than it is currently,” the report adds.
To combat AI-boosted ransomware attacks, the report recommends that cybersecurity teams implement “rigorous security controls,” access “timely and relevant threat intelligence” and adopt AI-enhanced cyber defense tools.
The report also lists tips and best practices for preventing and mitigating all types of ransomware attacks, including:
- Back up your data, system images and configurations; regularly test these backups; and keep them offline.
- Promptly and regularly patch and update your operating systems, applications and firmware.
- Develop an incident response plan and test it.
- Segment your networks.
- Take steps to limit your risk of getting breached if a trusted third-party with access to your network — like a supplier or contractor — gets hacked.
IT-ISAC also predicts that in 2025 ransomware groups will:
- Continue to target the critical infrastructure sector
- Expand their use of zero-day exploits
- Shift further towards double extortion and data theft tactics
- Refine their data exfiltration techniques
For more information about how AI is transforming ransomware:
- “Global ransomware threat expected to rise with AI” (U.K. National Cyber Security Centre)
- “AI making ransomware easier, more prevalent, committee hears” (The Hill)
- “AI-Driven Ransomware Group Strikes 85 Victims” (Bank Infosecurity)
- “AI-Powered Ransomware Attacks” (DZone)
- “FunkSec ransomware chases notoriety with AI-assisted code” (SC World)
3 - Tenable poll looks at security tool sprawl, integration
During our recent webinar “Security Beyond Silos with Tenable + Vulcan Cyber: Unified Exposure Management,” we polled attendees about topics including their level of security tool integration and the number of security tools they use for tasks such as asset discovery. Check out how they responded!
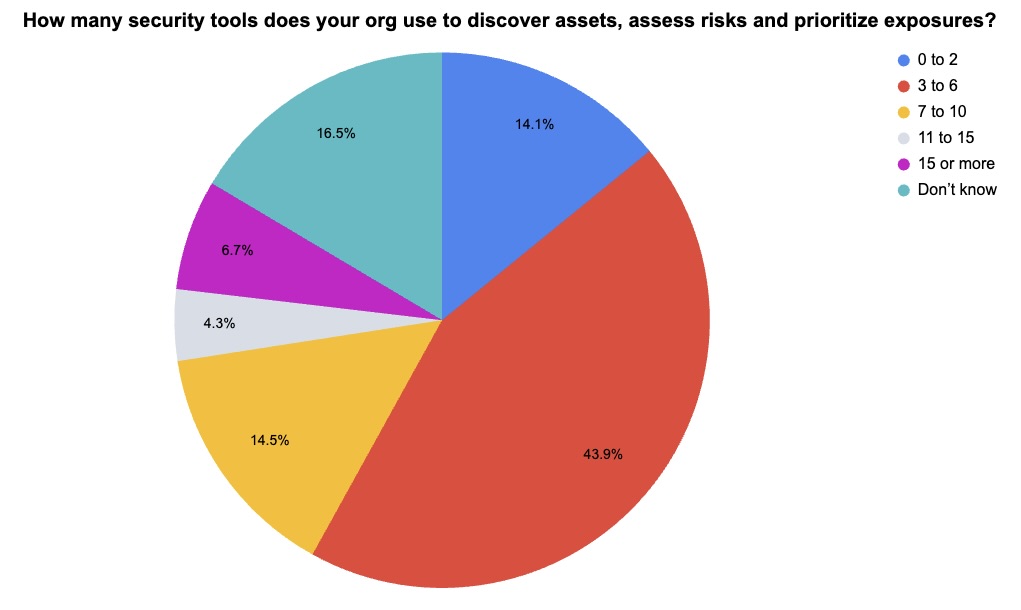
(255 webinar attendees polled by Tenable, February 2025)
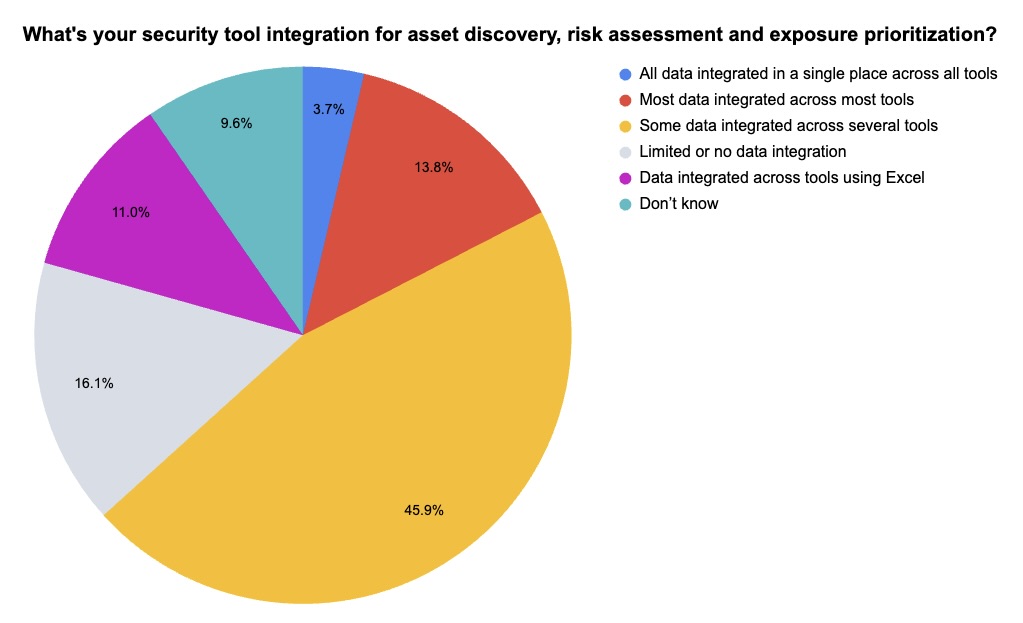
(218 webinar attendees polled by Tenable, February 2025)
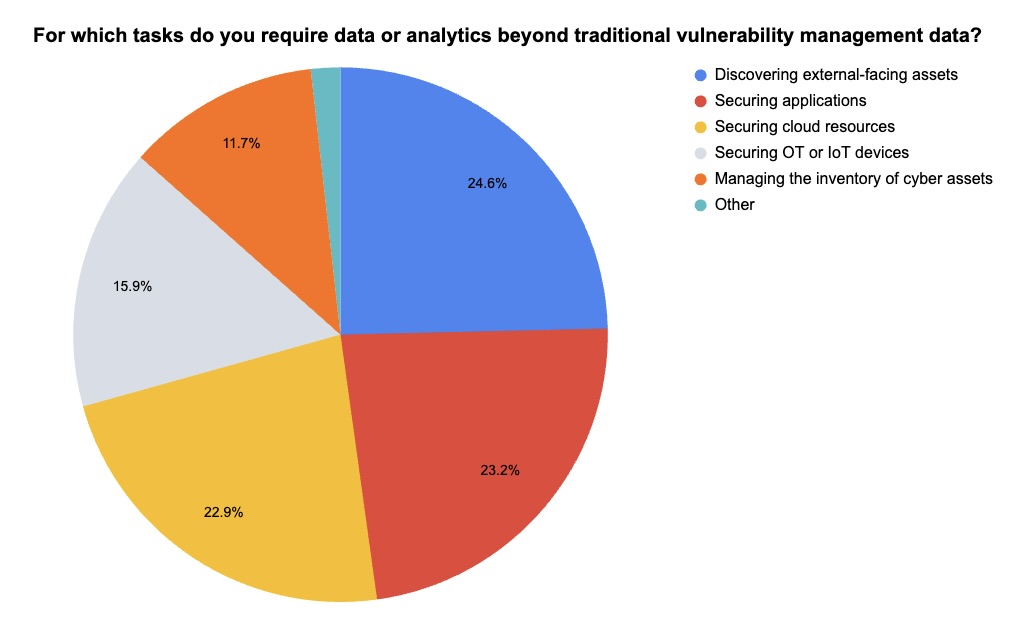
(Respondents could choose more than one answer. 277 webinar attendees polled by Tenable, February 2025.)
Interested in how to prioritize and address critical threats with unified visibility and enriched intelligence? Learn about unified exposure management by watching the on-demand webinar “Security Beyond Silos with Tenable + Vulcan Cyber: Unified Exposure Management.”
4 - Survey: As orgs pursue responsible AI, challenges remain
Businesses are wholeheartedly embracing AI, which in turn is fueling investments in data projects. However, a key success element for AI and data initiatives is still a work in progress: responsible AI.
That finding comes from the Data & AI Leadership Exchange’s “2025 AI & Data Leadership Executive Benchmark Survey,” for which 125 C-level executives, most of them Chief Data Officers from Fortune 1000 companies, were polled.
“Responsible AI is seen as an increasing priority for most organizations, as they focus on establishing safeguards and guardrails to ensure responsible AI utilization. More work needs to be done,” the report reads.
Specifically, surveyed organizations are concerned about misinformation and disinformation; ethical bias; job loss; and insufficient staffers skilled in responsible AI.

A strong majority of respondents say that investment in responsible AI is a top corporate priority (73.5%). While respondents’ belief that responsible AI safeguards must be in place is almost unanimous (97.5%), those safeguards are in place today at 77.6% of organizations.
Meanwhile, little over half of respondents (56.5%) said their organization has enough skilled employees to ensure the implementation of responsible AI. “Talent continues to be a limiting factor,” the report reads.
For more information about AI security, check out these Tenable blogs:
- “How AI Can Boost Your Cybersecurity Program”
- “6 Best Practices for Implementing AI Securely and Ethically”
- “How to Discover, Analyze and Respond to Threats Faster with Generative AI”
- “Securing the AI Attack Surface: Separating the Unknown from the Well Understood”
- “Harden Your Cloud Security Posture by Protecting Your Cloud Data and AI Resources”
5 - Report: Ransomware attacks up sharply in January
Ransomware groups had an unusually busy January, as attacks more than doubled year-on-year, a trend that further stresses the importance of practicing proactive cybersecurity.
Observed ransomware attacks reached 590 in January — up 3% compared with December 2024 and 114% year-on-year -- according to NCC Group’s “Cyber Threat Intelligence Review of January 2025” report, published this week.
“Taking action to mitigate these risks is more crucial than ever, with continuous monitoring, comprehensive training, and robust cyber security measures proving essential,” Matt Hull, Head of Threat Intelligence at NCC Group, said in a statement.
Factors that drove the surge in ransomware attacks included a more unstable geopolitical environment; the emergence of new ransomware groups; more effective attack methods and tools.
Other highlights from the report include:
- The Akira ransomware gang ranked first with 13% of all attacks.
- The most targeted sector was industrials, which received a quarter of all attacks, a sign of ransomware groups’ focus on critical infrastructure organizations.
- Among regions, North America suffered the majority of attacks (50%), followed by Europe (22%)
Top 10 ransomware groups in January 2025
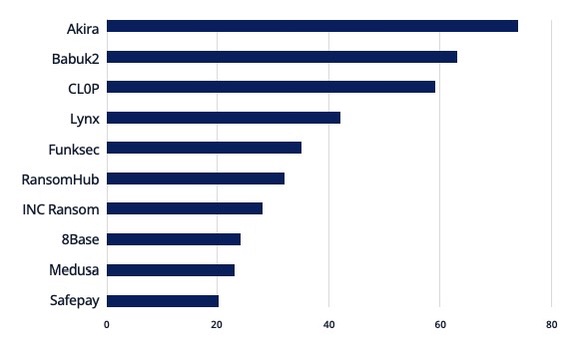
(Source: NCC Group’s “Cyber Threat Intelligence Review of January 2025” report, January 2025)
For more information about preventing and mitigating ransomware attacks:
- “Ransomware: How to prevent and recover” (Canadian Centre for Cyber Security)
- “3 Best Practices to Protect Backups from Ransomware” (TechTarget)
- “Steps to Help Prevent & Limit the Impact of Ransomware” (Center for Internet Security)
- “Preventing Ransomware Attacks at Scale” (Harvard Business Review)
- “Reporting ransomware attacks: Steps to take” (TechTarget)
6 - FBI: North Korea behind massive crypto theft
The North Korean government, acting via a hacking group known as TraderTraitor and as the Lazarus Group, is responsible for the recent mega-theft of $1.5 billion worth of cryptocurrency, the Federal Bureau of Investigation (FBI) said this week.
The North Korean cybercrime group stole the crypto funds from Dubai-based exchange Bybit in what is considered one of the largest crypto heists ever.
“TraderTraitor actors are proceeding rapidly and have converted some of the stolen assets to Bitcoin and other virtual assets dispersed across thousands of addresses on multiple blockchains,” reads the FBI’s public service announcement.
The FBI is asking entities involved in the crypto services sector to be on the lookout for transactions tied to the theft and to block them. The PSA includes a list of Ethereum addresses used to hold assets from the heist.
- AI
- Cloud
- Exposure Management
- Cloud
- Cybersecurity Snapshot
- Exposure Management
- Federal
- Government

