Cybersecurity Snapshot: Medusa Ransomware Impacting Critical Infrastructure, CISA Warns, While NIST Selects New Quantum-Resistant Algorithm

Check out how to protect your org against the Medusa ransomware gang. Plus, another cryptographic algorithm designed to resist quantum attacks will be standardized. Meanwhile, Tenable did a deep dive on DeepSeek’s malware-creation capabilities. And get the latest on vulnerability prioritization; CIS Benchmarks; and open source software risks.
Dive into six things that are top of mind for the week ending March 14.
1 - CISA: Hundreds of critical infrastructure orgs hit by Medusa ransomware
Don’t let the Medusa ransomware group turn your network into stone.
That’s the message the U.S. government sent this week via an advisory to cybersecurity teams, especially those at critical infrastructure organizations.
The advisory outlines Medusa’s tactics, techniques and procedures, as well as its indicators of compromise. It also provides mitigation recommendations, including patching known software vulnerabilities, segmenting networks and filtering network traffic.
Medusa, a ransomware-as-a-service variant, has impacted 300-plus critical infrastructure organizations in sectors like healthcare, education and manufacturing since mid-2021, according to the advisory, which is titled “#StopRansomware: Medusa Ransomware.”
“Medusa actors use common techniques like phishing campaigns and exploiting unpatched software vulnerabilities,” reads a statement from the U.S. Cybersecurity and Infrastructure Agency (CISA), which issued the joint advisory with the Federal Bureau of Investigation (FBI) and the Multi-State Information Sharing and Analysis Center (MS-ISAC).

Medusa attackers use a double extortion model, meaning they encrypt the victim’s data and threaten to publish it if the ransom isn’t paid.
Medusa leaders recruit initial access brokers (IABs), tasking them with gaining a foothold in victims’ networks. These IAB affiliates, who can earn up to $1 million, use common attack techniques that organizations can repel if they have a solid foundation of preventive cybersecurity practices and processes.
Other mitigation recommendations offered in the advisory include:
- Require multifactor authentication for as many services as possible.
- Assign user-access rights according to the principle of least privilege, and audit user accounts that have administrative privileges.
- Back up all of the organization’s data; encrypt it; and store it offline.
For more information about ransomware prevention and mitigation:
- “#StopRansomware Guide” (CISA)
- “A Look Inside the Ransomware Ecosystem” (Tenable)
- “Ransomware: How to prevent and recover” (Canadian Centre for Cyber Security)
- “How to prevent ransomware in 6 steps” (TechTarget)
- “Healthcare is an ‘easy victim’ for ransomware attacks. How hospitals can mitigate the damage.” (Healthcare Dive)
2 - NIST picks another quantum-resistant algorithm
The number of algorithms for securing data against quantum-computer cyberattacks continues to grow.
This week, the U.S. National Institute of Standards and Technology (NIST) picked the fifth algorithm for post-quantum encryption.
Known as HQC, the general-encryption algorithm will be able to protect stored and in-transit data. NIST envisions HQC as a backup for ML-KEM, a general-encryption, quantum-resistant algorithm released last year.
If ML-KEM is cracked, HQC could be used instead, because, according to NIST, the two algorithms were developed using “a different math approach.”
“As we advance our understanding of future quantum computers and adapt to emerging cryptanalysis techniques, it’s essential to have a fallback in case ML-KEM proves to be vulnerable,” Dustin Moody, who heads NIST’s Post-Quantum Cryptography project, said in a statement.
However, unlike ML-KEM, HQC isn’t ready to be deployed yet. NIST plans to release a draft standard for HQC in about a year, followed by a 90-day comment period. The HQC standard is slated for release in 2027.

In addition to ML-KEM, NIST released two other quantum-resistant algorithm standards last year: ML-DSA, envisioned as the primary standard for protecting digital signatures; and SLH-DSA, also designed for digital signatures. The three standards contain the encryption algorithms’ computer code, implementation instructions and their intended uses.
NIST expects to release a fourth quantum-resistant algorithm standard in 2026.
Here’s the problem these algorithms are designed to solve. Quantum computers will be so powerful that they’ll be able to decrypt data protected with today’s public-key cryptographic algorithms. Although it’s not clear when these super powerful computers will become available, the consensus is that it’ll be sometime between 2030 and 2040.
Meanwhile, governments, academia and industry groups are urging organizations to start transitioning to quantum-resistant encryption now, because they process requires detailed planning and careful deployment.
To help organizations with this migration process, NIST last week published a draft white paper titled “Considerations for Achieving Crypto Agility.”
“Crypto agility describes the capabilities needed to replace and adapt cryptographic algorithms for protocols, applications, software, hardware, and infrastructures without interrupting the flow of a running system to achieve resiliency,” reads a NIST statement about the new publication.
Topics addressed in the white paper include interoperability challenges arising from the transition; cryptographic key establishment; and API usage in a crypto library application.
For more information about how to protect your organization against the quantum computing cyberthreat:
- “How to prepare for a secure post-quantum future” (TechTarget)
- “Moody’s sounds alarm on quantum computing risk, as transition to PQC ‘will be long and costly’” (Industrial Cyber)
- “Companies Prepare to Fight Quantum Hackers” (The Wall Street Journal)
- “US unveils new tools to withstand encryption-breaking quantum. Here's what experts are saying” (World Economic Forum)
- “Quantum is coming — and bringing new cybersecurity threats with it” (KPMG)
- “Quantum and the Threat to Encryption” (SecurityWeek)
3 - Tenable researches DeepSeek’s malware-creation capabilities
To what extent could attackers use the generative AI tool DeepSeek to create malware, such as keyloggers and ransomware?
That’s a question Tenable Research set out to answer via a detailed analysis of the popular open-source product, which is owned by a Chinese AI company also called DeepSeek.
The short answer: The DeepSeek R1 large language model (LLM) can provide a useful starting point for developing malware, but it requires additional prompting and debugging.

“At its core, DeepSeek can create the basic structure for malware,” Tenable Staff Research Engineer Nick Miles wrote this week in a blog post detailing the findings.
“However, it is not capable of doing so without additional prompt engineering as well as manual code editing for more advanced features,” he added.
To get all the details, read the blog “DeepSeek Deep Dive Part 1: Creating Malware, Including Keyloggers and Ransomware.”
The DeepSeek probe is part of Tenable Research’s ongoing security analysis of generative AI tools, a topic that’s top of mind for many security leaders, as they seek guidance on how to protect their organizations against AI-boosted cyberattacks.
For more information about AI security, check out these Tenable blogs:
- “Frequently Asked Questions About DeepSeek Large Language Model (LLM)”
- “How AI Can Boost Your Cybersecurity Program”
- “6 Best Practices for Implementing AI Securely and Ethically”
- “How to Discover, Analyze and Respond to Threats Faster with Generative AI”
- “Securing the AI Attack Surface: Separating the Unknown from the Well Understood”
4 - Report outlines tips for addressing open source software risks
Looking to boost open source security? Check out the latest publication offering best practices for managing and mitigating risks associated with the use of open source software (OSS).
“Open Source Software Best Practices and Supply Chain Risk Management,” a report published by the U.K. Department for Science, Innovation and Technology, draws from guidance provided by governments, industry groups and standards bodies about open source software’s security and supply chain risks.
However, the report has distilled and analyzed the guidance so that it applies to organizations of all sizes and industries. “Due to the broad and evolving view of OSS best practices, our research found discrepancies and variations in approaches to OSS adoption, management, and community engagement,” the report reads.

The report focuses on four core best practices for open source software security:
- Establish an internal policy addressing elements including:
- A list of acceptable open source software licenses
- A list of projects in which open source software can be allowed
- Criteria for assessing the security and maturity of open source software components
- The stringency levels with which different types of open source software components will be evaluated
- The approval process for open source software components
- Create a software bill of materials (SBOM) that lists the components and dependencies in the open source software your organization builds.
- Continuously monitor the supply chain of the open source software used by your organization to identify vulnerabilities and licensing issues.
- Actively engage with the OSS community to, for example, foster innovation, enhance the quality of OSS components and attract new talent.
For more information about open source software security:
- “Security considerations when using open source software (Canadian Centre for Cyber Security)
- “The Shifting Landscape of Open Source Security” (Dark Reading)
- “Top 10 open source software security risks — and how to mitigate them” (CSO)
- “Seven ways to secure open-source software” (SC World)
- “Maintainer Perspectives on Open Source Software Security” (Linux Foundation)
5 - Tenable poll looks at vulnerability prioritization
During our recent webinar “Tenable Vulnerability Management Customer Update,” we took the opportunity to poll attendees about their vulnerability prioritization processes and challenges. Check out what they said!
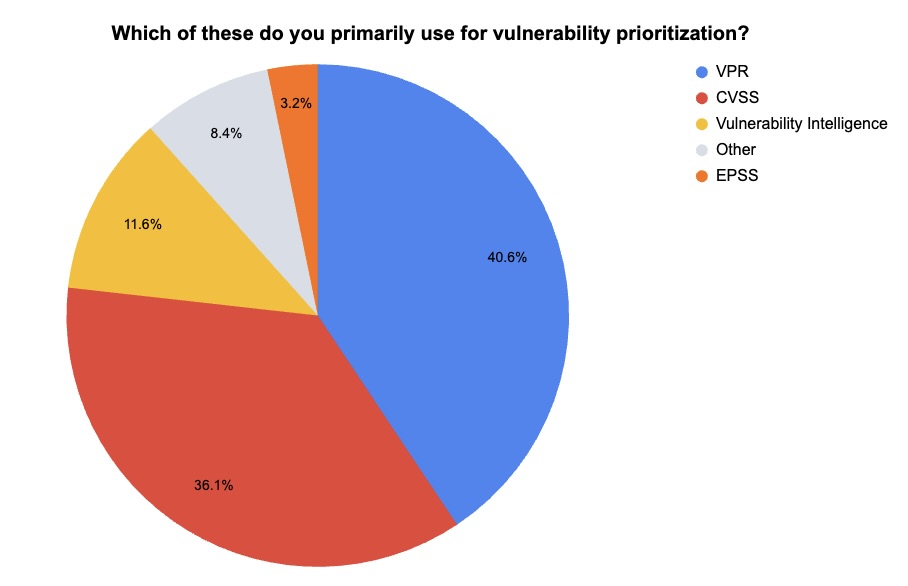
(155 webinar attendees polled by Tenable, March 2025)
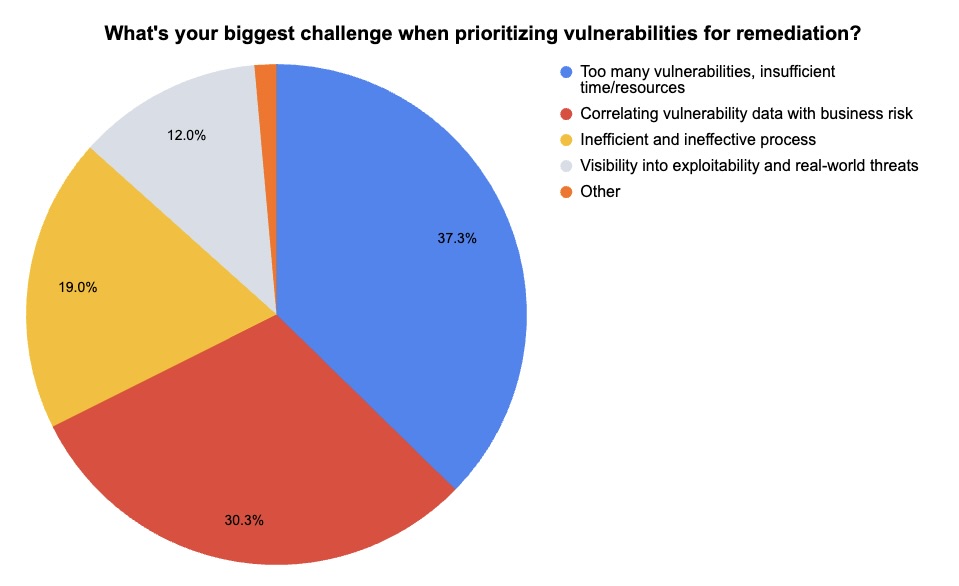
(142 webinar attendees polled by Tenable, March 2025)
To learn more about approaches to prioritization using Tenable Vulnerability Management’s Vulnerability Intelligence feature, watch the on-demand webinar “Tenable Vulnerability Management Customer Update.”
6 - CIS Benchmarks for Oracle, Apache and SUSE products get an update
This one’s for you if you use the Center for Internet Security (CIS) Benchmarks’ secure-configuration guidelines to harden your products against attacks.
CIS recently announced Benchmark updates for Apache Tomcat, Oracle Cloud Infrastructure and SUSE Linux Enterprise. These are the specific product versions whose Benchmarks were updated:
- CIS Apache Tomcat 10.1 Benchmark v1.1.0
- CIS Oracle Cloud Infrastructure Foundations Benchmark v3.0.0
- CIS SUSE Linux Enterprise 15 Benchmark v2.0.1

CIS also released a brand new Benchmark for Apache Tomcat 11.0.
To get more details, read the CIS blog “CIS Benchmarks March 2025 Update.” For more information about the CIS Benchmarks list, check out its home page, as well as:
- “Getting to Know the CIS Benchmarks” (CIS)
- “Security Via Consensus: Developing the CIS Benchmarks” (Dark Reading)
- “How to Unlock the Security Benefits of the CIS Benchmarks” (Tenable)
- “CIS Benchmarks Communities: Where configurations meet consensus” (Help Net Security)
- “CIS Benchmarks: DevOps Guide to Hardening the Cloud” (DevOps)
- AI
- Cloud
- Exposure Management
- Industrial Control Systems Monitoring
- IT/OT
- Risk-based Vulnerability Management
- Cloud
- Cybersecurity Snapshot
- Federal
- Government
- Risk-based Vulnerability Management
- SCADA


