Cybersecurity Snapshot: Russia-backed Hackers Aim at Critical Infrastructure Orgs, as Crypto Fraud Balloons

Critical infrastructure operators must beware of Russian military hacking groups. Plus, cyber scammers are having a field day with crypto fraud. Meanwhile, AI and cloud vendors face stricter reporting regulations in the U.S. And get the latest on AI-model risk management and on cybersecurity understaffing!
Dive into six things that are top of mind for the week ending September 13.
1 - Critical infrastructure orgs targeted by Russia-backed hackers
Here’s an important warning for critical infrastructure organizations in the U.S. and abroad: Nation-state hacking groups affiliated with Russia’s military are attacking critical infrastructure targets to conduct espionage, carry out sabotage and inflict reputational harm.
That’s according to a joint advisory from the governments of the U.S. and nine other countries that details the groups’ tactics, techniques and procedures, lists indicators of compromise and offers mitigation recommendations.
The groups are affiliated with the Russian armed forces’ Unit 29155, according to the advisory “Russian Military Cyber Actors Target US and Global Critical Infrastructure” published by the U.S. Cybersecurity and Infrastructure Security Agency (CISA).
These Unit 29155 groups have been operating since 2020. They’re currently focused on disrupting aid efforts to Ukraine, which they first attacked with the WhisperGate malware in early 2022.

They also target critical infrastructure organizations in North Atlantic Treaty Organization (NATO) countries. Their attacks include defacing websites, stealing and leaking data, and scanning infrastructure.
To gain initial access, these hacking groups use VPNs to hide their actions and then target internet-facing systems’ weaknesses, including these vulnerabilities:
Immediate steps that critical infrastructure organizations should take to protect themselves include:
- Make it a priority to routinely update systems and to remediate known vulnerabilities exploited in the wild.
- Segment networks.
- Adopt phishing-resistant multi-factor authentication for all externally-facing account services.
To get more details, read:
- The CISA alert
- The full advisory “Russian Military Cyber Actors Target US and Global Critical Infrastructure”
To learn more about securing operational technology (OT) systems in critical infrastructure environments, check out these Tenable resources:
- “CISA Finding: 90% of Initial Access to Critical Infrastructure Is Gained Via Identity Compromise. What Can You Do About It?” (blog)
- “OT Security Master Class: Understanding the Key Principles, Challenges, and Solutions” (on-demand webinar)
- “Operational Technology (OT) Security: How to Reduce Cyber Risk When IT and OT Converge” (guide)
- “5 Key OT Security Use Cases For The DoD: Safeguarding OT Networks and Cyber-Physical Systems” (white paper)
- “Unlock Advanced IoT Visibility in your OT Environment Security” (on-demand webinar)
2 - Cyber crooks double down on crypto scams
Decentralized. Distributed. Speedy. Ephemeral. Irreversible.
These are some of the key characteristics of cryptocurrency transactions that make them irresistibly attractive to cybercriminals, as evidenced by a strong increase in both the number of crypto scams and total losses in 2023.
These findings come from the “2023 IC3 Cryptocurrency Report,” released this week by the FBI’s Internet Crime Complaint Center (IC3). Specifically, the IC3 received almost 69,500 crypto-related complaints last year. Losses amounted to $5.6 billion, a 45% increase over 2022.
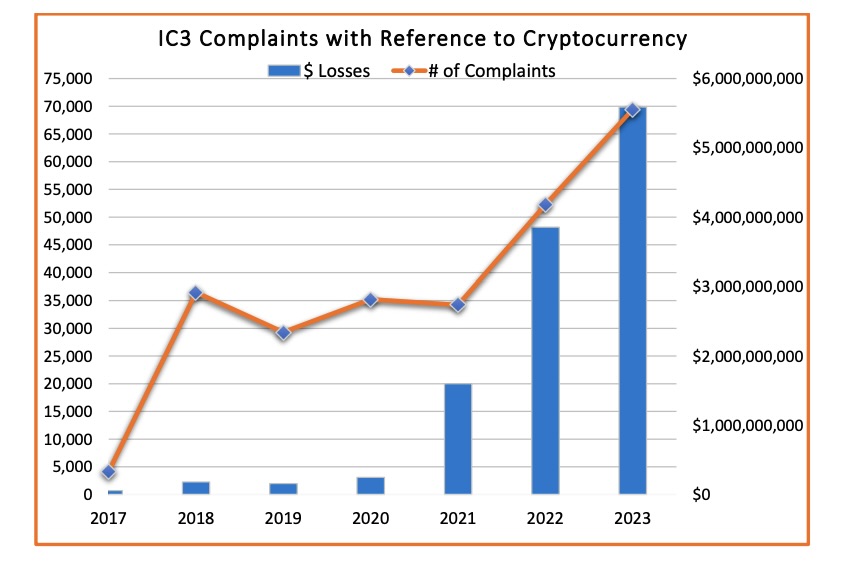
(Source: “2023 IC3 Cryptocurrency Report” from the FBI’s Internet Crime Complaint Center, September 2024)
Other report takeaways include:
- Most of the losses – 70% – came from investment scams.
- Crypto scams accounted for about 10% of all financial-fraud complaints, but they disproportionately generated almost 50% of total losses.
- While most of the complaints fielded by IC3 originated in the U.S., it received complaints from victims in 200-plus countries.
The report unpacks multiple types of crypto investment-fraud schemes, detailing scammers’ tactics and offering detailed prevention tips.
For more information about crypto fraud:
- “What To Know About Cryptocurrency and Scams” (U.S. Federal Trade Commission)
- “How To Recover Funds From Crypto and Bitcoin Scam” (Blockchain Council)
- “Cryptocurrency Scams: How to Spot, Report, and Avoid Them” (Investopedia)
- “Cryptocurrency scams: Common types and prevention” (TechTarget)
VIDEO
How Americans Are Losing Their Life Savings To Crypto Fraud (CNBC)
3 - Uncle Sam wants more info from AI and cloud vendors
The AI regulatory landscape continues to expand.
This week, developers of AI systems and providers of cloud services learned they may soon have to submit more detailed reports about their wares to the U.S. government.
Specifically, the U.S. Department of Commerce has proposed new rules for mandatory and detailed reporting about AI models and cloud computing clusters, due to concerns about hackers abusing powerful AI and cloud systems.
AI developers and cloud providers would have to submit information to the U.S. government about their development activities and about cybersecurity measures and testing.
“This proposed rule would help us keep pace with new developments in AI technology to bolster our national defense and safeguard our national security,” Secretary of Commerce Gina M. Raimondo said in a statement.
To get more information about trends in AI security and regulation:
- “AI governance trends: How regulation, collaboration and skills demand are shaping the industry” (World Economic Forum)
- “Artificial Intelligence Index Report 2024: Policy and Governance” (Stanford University)
- “Legalweek 2024: Current US AI regulation means adopting a strategic – and communicative – approach” (Thomson Reuters)
- “AI regulation: What businesses need to know in 2024” (TechTarget)
4 - New risk management framework for AI and ML models
Concerned about the pitfalls faced by developers and users of AI and machine learning (ML) models? You might want to check out the Cloud Security Alliance’s paper “AI Model Risk Management Framework.”
The 54-page document addresses common AI model risks, including:
- Data quality issues
- Flawed model selection, tuning and design
- Implementation and operational mistakes
The CSA framework offers a “structured approach” to identify, assess, mitigate and monitor AI model risks. Its four pillars are:
- Model cards, which detail model elements such as its purpose, training, capabilities, resistance to attacks, limitations and performance
- Data sheets, which offer descriptions of the dataset used to create an AI model
- Risk cards, which summarize an AI model’s key risks
- Scenario planning, which outlines ways in which a model could malfunction or be abused
Framework Pillars for Responsible and Well-Informed Use of AI / ML
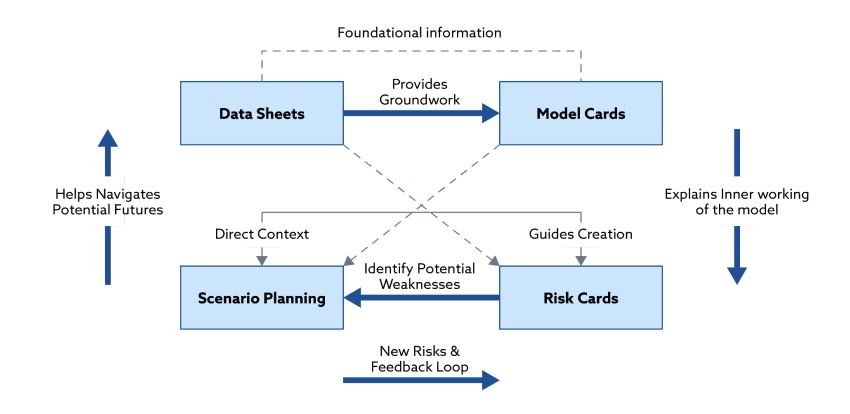
(Source: Cloud Security Alliance’s “AI Model Risk Management Framework,” July 2024)
“A comprehensive framework goes a long way to ensuring responsible development and enabling the safe and responsible use of beneficial AI/ML models, which in turn allows enterprises to keep pace with AI innovation,” Caleb Sima, Chair of the CSA AI Safety Initiative, said in a statement.
The paper’s intended audience includes AI and ML engineers and developers; data scientists; risk managers; compliance pros; and business executives.
According to the paper, the benefits of adopting a risk management framework for AI and ML models include more transparency, proactive risk mitigation and enhanced decision-making processes.
5 - U.S. gov’t tackles cyber understaffing with new campaign
Is your organization struggling to recruit cybersecurity pros? A new initiative from the U.S. government aims to connect potential candidates with employers.
With about 500,000 cybersecurity jobs vacant in the U.S., the White House has launched a two-month “sprint” campaign designed to help recruit candidates to fill these positions.
Called “Service for America,” the campaign kicked off in early September and runs through the end of October. Its goal: to boost the country’s cyber workforce via a variety of initiatives, such as job fairs.
“These jobs offer an opportunity to serve our country by protecting our national security, while also offering a personal path to prosperity,” Nation Cyber Director Harry Coker, Jr. wrote in the blog post “Service for America: Cyber Is Serving Your Country.”
“Service for America” will aim to create awareness that people don’t need a technical degree or background to qualify for cybersecurity jobs. “Cyber professionals are part of a dynamic and diverse modern workforce and individuals from all backgrounds and disciplines have a place,” Coker, Jr. wrote.

“Service for America” is part of the “National Cyber Workforce and Education Strategy,” unveiled in mid-2023, which seeks, among other things, to:
- Remove degree requirements from cybersecurity jobs, shifting instead to a skills-based approach
- Expand apprenticeships that allow people to gain cybersecurity skills while at their current jobs
- Encourage employers, academia, local governments and non-profit organizations to offer cybersecurity training and education in their local communities
The Office of the National Cyber Director is spearheading the “Service for America” campaign, in partnership with the Office of Management and Budget and the Office of Personnel Management.
To get more details, check out:
- The “Service for America” home page
- The blog post “Service for America: Cyber Is Serving Your Country”
- This video from the National Cyber Director
For more information about how organizations can improve recruitment of cyber pros:
- “Recruitment and Retention in Cybersecurity” (ISC2)
- “Strategic Cybersecurity Talent Framework” (World Economic Forum)
- “Growing threats outpace cybersecurity workforce” (Thomson Reuters)
- “Why closing the cyber skills gap requires a collaborative approach” (World Economic Forum)
- “Cybersecurity skills gap: Why it exists and how to address it” (TechTarget)
6 - Report: Almost 5M cyber jobs open globally
And continuing with the topic of cybersecurity understaffing, the problem isn’t getting any better globally either.
There are 4.8 million vacant cybersecurity jobs worldwide, up 19% compared with 2023, with the primary causes being budget constraints and lack of qualified candidates, according to the “2024 ISC2 Cybersecurity Workforce Study.”
The number of cyber pros employed globally – 5.5 million – stayed flat from last year. Meanwhile, the world needs 10.2 million cyber pros to satisfy the workforce demand.
“At a time when organizations can least afford the cost, disruption and reputational damage of a cybersecurity incident, the profession is under its greatest pressure to maintain safety and security with fewer resources,” reads an ISC2 statement.
ISC2 plans to publish the report in October, but released key stats this week.
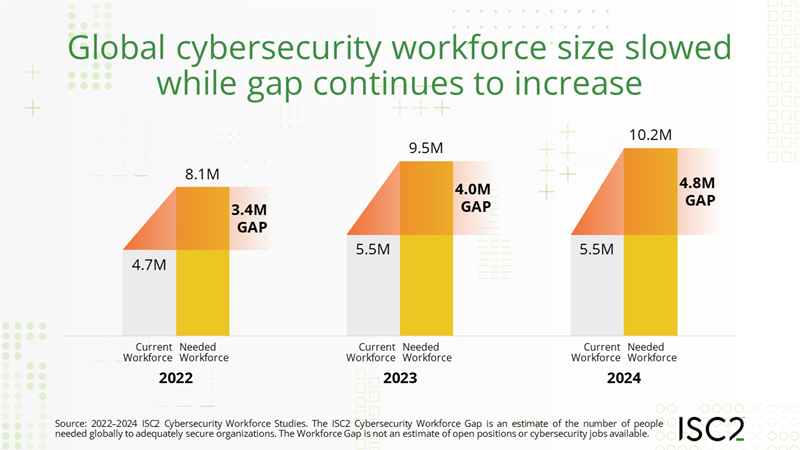
Another number that stayed flat compared with 2023 was the percentage of respondents that reported having a shortage of cyber pros – 67%.
In addition to understaffing, organizations are also experiencing skills gaps. Specifically, 90% reported having technical skills gaps in their cybersecurity teams, with AI / ML skills the most commonly reported at 34%.
Rounding out the top five cybersecurity tech-skills gaps were:
- Cloud computing security (30%)
- Zero Trust implementation (27%)
- Digital forensics and incident response (25%)
- A tie between application security and penetration testing, both at 24%
Meanwhile, 74% of respondents described the current threat landscape as the most challenging they’ve encountered in the last five years
The study is based on a worldwide survey of almost 16,000 cybersecurity practitioners and decision-makers.
If you’d like to explore career opportunities at Tenable, visit us at https://www.tenable.com/careers
- Cloud
- Industrial Control Systems Monitoring
- IT/OT
- Risk-based Vulnerability Management
- Cloud
- Cybersecurity Snapshot
- Federal
- Government
- Internet of Things
- OT Security
- Risk-based Vulnerability Management


