Reducing Remediation Time Remains a Challenge: How Tenable Vulnerability Watch Can Help
Timely vulnerability remediation is an ongoing challenge for organizations as they struggle to prioritize the exposures that represent the greatest risk to their operations. Existing scoring systems are invaluable but can lack context. Here’s how Tenable’s Vulnerability Watch classification system can help.
Background
Over the past six years working in Tenable’s research organization, I’ve watched known vulnerabilities and zero-day flaws plague organizations in the immediate aftermath of disclosure or even years afterwards. Following each blog post or threat report we’ve published, I kept coming back to the same question: Why are so many organizations struggling to remediate vulnerabilities in a timely manner?
As someone who followed the evolution of COVID-19 variants throughout the beginning of the pandemic, I saw that the World Health Organization (WHO) began to label new variants under a classification system as the virus began to mutate. This classification system was designed to help prioritization efforts for monitoring and research. It included accessible labels like variants of interest and variants of concern to help communicate urgency and focus global attention.
I began to wonder: What if we borrowed from the same type of classification system used by the WHO and applied it to vulnerability intelligence? Numeric-based systems like the Common Vulnerability Scoring System (CVSS) and Exploit Prediction Scoring System (EPSS) provide mechanisms for prioritization based on scoring. However, they don’t always provide enough context to help decision makers. So, what if we used simple, clear and status-based terminology to communicate risks surrounding vulnerabilities in order to guide action?
This led us to develop Vulnerability Watch, a classification system for vulnerabilities inspired by the WHO’s classification of COVID-19 variants. Vulnerability Watch is a small, but important part of Tenable’s Vulnerability Intelligence offering that was launched in 2024. Now, in addition to being available in product, Vulnerability Watch classifications can be found on the Tenable CVE page, as well as within individual CVE pages for select vulnerabilities that have been classified under the Vulnerability Watch.
In this blog, we discuss some of the challenges organizations face when it comes to vulnerability prioritization and remediation and how a classification system like Vulnerability Watch can help.
If everything is important, nothing is important
CVSS is the most widely used metric when assigning a severity score for Common Vulnerabilities and Exposures (CVEs). CVSS scores are assigned by a vendor and or an authority like the National Institute of Standards and Technology (NIST). Each CVE score is based on various metrics from exploitability to impact, with a corresponding severity level tied to these scores. Severity levels include low, medium, high and critical.
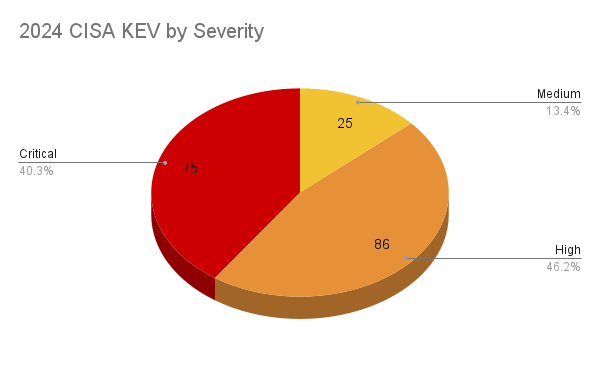
When looking at repositories, such as the Cybersecurity and Infrastructure Security Agency (CISA) Known Exploited Vulnerabilities (KEV) catalog, we can make observations about severity and vulnerability risk. In 2024, CISA added a total of 186 CVEs to the KEV.
Source: Tenable Research
Four in ten (40%) of these 186 CVEs were rated as critical. The remaining 60% was made up of high severity vulnerabilities (46.2%) and medium vulnerabilities(13.4%). This underscores that severity alone is not enough when it comes to making decisions around vulnerability prioritization.
Remediation rates underscore a need for more clarity
While the KEV serves as a valuable resource for security practitioners, we still see many organizations not patching these critical flaws in a timely manner. Despite the severity and inclusion on the KEV, our research has found an overall trend of poor remediation rates.
This trend was highlighted as part of a collaboration with Verizon on the 2025 Data Breach Investigations Report (DBIR). Tenable Research analyzed over 160 million data points and evaluated the remediation rates for a list of 17 CVEs in edge devices highlighted in the DBIR. Of the 17 CVEs, over half (52.9%) were non-critical flaws (less than 9.0 CVSS scores).
We also analyzed average remediation rates for these CVEs across various industry sectors. Through this analysis, we found many industries faced challenges with remediating many of these flaws. For instance, CVE-2024-21762 and CVE-2024-23113, a pair of critical Fortinet flaws, had very long remediation rates, averaging between 172 days and 260 days. Even CVE-2024-3400, a critical vulnerability in Palo Alto Networks PAN-OS assigned the maximum CVSS score of 10.0, also saw most industries average over 100 days to remediate the flaw.
There are a variety of reasons why organizations may struggle with remediation — including organizational siloes, operational downtime required to patch systems, and difficulty determining how to prioritize vulnerabilities based on the risk they represent. While existing scoring systems provide invaluable guidance, we believe additional context is needed in order to improve remediation times.
A semantic layer for vulnerability intelligence
Our Vulnerability Watch classifications are not a replacement for CVSS, EPSS or any other scoring metric. Those still serve a distinct purpose in vulnerability prioritization. We also recognize that cybersecurity teams are often inundated by a deluge of alerts and it can be difficult at times to separate the signal from the noise. These vulnerability watch classifications offer a semantic layer to help translate risk into terminology that is easier to understand for various stakeholders in remediation efforts.
Tenable’s Vulnerability Watch classifications
Vulnerability Watch includes the following classifications: vulnerability being monitored, vulnerability of interest and vulnerability of concern. The following are short descriptions of each classification.
Vulnerability Being Monitored
A vulnerability being monitored (VBM) is a vulnerability that has the potential to impact customers of a particular software or hardware and is being actively tracked and researched by Tenable Research. VBMs may quickly evolve into Vulnerabilities of Interest (VOIs) or Vulnerabilities of Concern (VOCs) if a proof-of-concept (PoC) or exploitation is discovered, or if additional intelligence indicates that special attention should be given to this vulnerability. VBMs are actively monitored and elevated to VOI/VOC status should Tenable’s Vulnerability Intelligence justify an escalation of vulnerability status.
A few recent examples of VBMs include CVE-2024-48887, an unverified password change vulnerability in FortiSwitch, and CVE-2025-23120, a remote code execution flaw in Veeam Backup and Replication.
Vulnerability of Interest
A vulnerability of interest (VOI) is a vulnerability that meets the criteria of a VBM, but for which additional intelligence indicates that risk of impacts to customers is elevated or demonstrated through the publication of a PoC or details that could be used to craft a PoC along with initial reports of exploitation.
A few recent examples of VOIs include CVE-2025-22457, which was exploited by a China-Nexus threat actor known as UNC5221, and CVE-2025-32433, a remote code execution flaw in Erlang/OTP SSH.
Vulnerability of Concern
A Vulnerability of Concern (VOC) is a vulnerability that meets the criteria of a VOI, but for which active, widespread exploitation is imminent or ongoing. For VOCs, the ease of exploitation combined with severity of the issue may lead us to believe that widespread exploitation is imminent, if it has not already begun. Maintainers of software or devices vulnerable to VOCs can expect to see exploitation attempts and probing for vulnerable assets.
A few recent examples of VOCs include a pair of ConnectWise Screen Connect vulnerabilities (CVE-2024-1709, CVE-2024-1708) and Citrix Bleed (CVE-2023-4966).
The classifications are also flexible: a CVE can be reclassified from VBM to VOI, from VOI to VOC, or even from VOC back to VOI as risk context evolves.
Conclusion
We know there’s no single panacea for the challenges of vulnerability prioritization and remediation. These challenges require a multi-pronged approach. Backed by Tenable Research experts, our Vulnerability Watch classifications can help demystify some of the complexities introduced by CVSS and EPSS and provide stakeholders a simpler, more intuitive way to assess and prioritize risks posed by emerging threats that can contribute to faster responses and remediation.
Our Vulnerability Watch classifications can now be found on our CVE page.
Get more information
- Tenable Vulnerability Intelligence and Exposure Response
- Turning Data into Action: Intelligence-Driven Vulnerability Management
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable One, the Exposure Management Platform for the modern attack surface.
- Exposure Management
- Vulnerability Management
- Exposure Management
- Vulnerability Management


