Tenable Nessus Expands Attack Surface Coverage with Web Application Scanning

Web applications can be an Achilles’ heel for even the most mature security organizations. For small- and medium-sized businesses, as well as the security consultants and pen testers who support them, unsecured web apps can be a pathway to a data breach that can bring an organization to its knees. Here’s how Tenable Nessus can help.
When Tenable Nessus was launched in 1998, the attack surface consisted of only traditional IT devices — desktops, workstations, network equipment, etc. With the emergence of new technologies, the modern attack surface has expanded and threat actors are taking advantage of these new areas to infiltrate countless networks.
For security consultants, penetration testers, cloud security practitioners and small- and mid-sized businesses (SMBs), keeping up is a constant struggle. Securing the modern attack surface often involves cobbling together different security tools to address different attack surfaces. Even then, it’s difficult to gain a complete picture from an array of siloed solutions, possibly leaving the organization exposed to unknown risks.
What is needed is a fast, easy way to proactively find, prioritize and remediate vulnerabilities — on whatever attack surface they may be found. A solution whose assessment capabilities evolve as the modern attack surface evolves. What’s needed is Tenable Nessus Expert.
In addition to identifying vulnerabilities and misconfigurations in traditional IT devices, Nessus Expert helps secure your external attack surface by identifying internet-connected subdomain assets and assessing them for vulnerabilities. It also enables organizations to scan cloud infrastructure as code (IaC) repositories to identify security weaknesses before pushing them to production instances where they are harder, and more expensive, to fix.
And, today, with the release of Nessus 10.6, Tenable addresses another critical aspect of the modern attack surface — the security of web applications.
The way in: vulnerable web apps
According to a report from Siteefy, there are over 1 billion web applications around the world, with the vast majority being easily accessible to external users by design. Unfortunately, a report on web vulnerabilities from Invicti Security found that 63% of the websites they examined had either MEDIUM or HIGH severity vulnerabilities. This leads to millions of high-risk web app vulnerabilities that threat actors can target. It’s no surprise that Verizon’s 2023 Data Breach Investigations Report listed web applications as being the entry point for 25% of data breaches.
Web applications can have a wide range of complexity. Even the most simple web application is built with multiple layered third-party components, like web servers, web application servers, web frameworks, programming languages and JavaScript libraries. The problem for security teams is that many of these components are outdated and contain multiple high-risk vulnerabilities. Making matters worse, security teams often lack visibility into third-party components. In a commissioned study conducted by Forrester Consulting on behalf of Tenable1, nearly 50% of cybersecurity pros said they have moderate to no visibility into third-party software code vulnerabilities, while a third (36%) said the same for open source software code vulnerabilities. While common web vulnerabilities — like those identified by the Open Web Application Security Project (OWASP) — are often used for targeted attacks, third-party component vulnerabilities are being weaponized for use in automated attacks that look for vulnerable components to exploit.
Modern web applications are also constantly changing. As a result of this and other factors, the vast majority of an organization’s web applications may not be secured against critical vulnerabilities and misconfigurations that could bring a business to its knees and halt all customer transactions.
The way out: web application scanning with Nessus 10.6
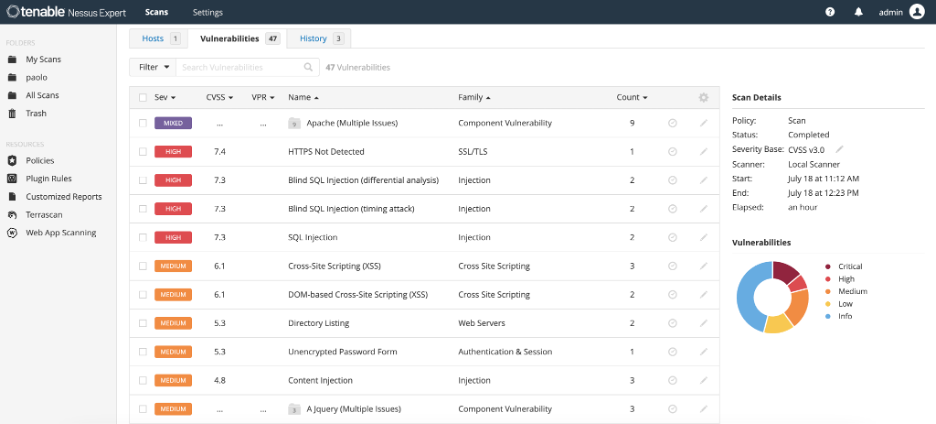
The web application scanning feature in Nessus provides simple, yet comprehensive, vulnerability scanning for modern web applications. It is designed for security practitioners to quickly create scans and get actionable results to address web application vulnerabilities.
Nessus 10.6 reduces the complexity of the task by leveraging the Nessus solution to launch new scans, analyze and drill into scan results and prioritize vulnerabilities for remediation. Its accurate vulnerability analysis leads to fewer false positives and negatives, ensuring that organizations understand the true risks associated with their web applications. And it offers safe scanning that ensures production web applications are not disrupted or delayed while they are being scanned.
Web app scanning in Nessus is a dynamic application security testing (DAST) feature that:
- identifies OWASP Top 10 vulnerabilities (e.g., cross-site scripting [XSS], SQL injection) in custom application code;
- identifies vulnerable versions of third-party components that make up the bulk of the application; and
- identifies common web app cyber hygiene issues related to SSL/TLS certificates and HTTP header misconfigurations.
Addressing all three categories of vulnerabilities are essential to ensuring comprehensive vulnerability coverage in modern web applications.
And, because its vulnerability detection capabilities are backed by Tenable Research, web app scanning in Nessus gains all the benefits this world-class research organization provides: number one in CVE coverage, number one in scan accuracy and speed of new vulnerability detections. As new dangerous web app vulnerabilities are discovered by our Security Response Team, vulnerability detections are quickly added to Nessus, giving you confidence that you aren’t wasting time remediating false positives or missing vulnerabilities that could be leveraged by an attacker.
Security consultants, pen testers, cloud security practitioners and SMBs continually struggle to keep up with the modern attack surface, and frequently need to use and combine multiple security tools that still leave them blind and exposed to unknown risks. They need a vulnerability assessment solution that not only addresses traditional IT assets and the modern attack surface of today, but one they can also have the confidence in that it will continue to enhance its coverage as that attack surface changes
In Tenable Nessus, they have it.
1A commissioned study of 825 cybersecurity and IT professionals conducted by Forrester Consulting on behalf of Tenable, May 2023.
Author’s note: The web application scanning capabilities now available in Tenable Nessus Expert 10.6 can also be found in Tenable Vulnerability Management (formerly Tenable.io). See the Learn More section for links to blogs that deal with different aspects of web application scanning. I hope you will find them educational and applicable to your experiences with web application scanning in Nessus Expert.
Learn more
- This Is How to Do Simple, Fast and Accurate Web App Security
- Identifying XML External Entity: How Tenable.io Web Application Scanning Can Help
- Identifying Server Side Request Forgery: How Tenable.io Web Application Scanning Can Help
- How to Use Tenable.io WAS to Find and Fix Sensitive Information Exposure in Microsoft Power Apps
- Identifying Prototype Pollution Vulnerabilities: How Tenable.io Web Application Scanning Can Help
- Web Application Scanning
- Vulnerability Management

