Tenable Roundup for Microsoft's June 2019 Patch Tuesday

The SandboxEscaper privilege escalation bugs are among the nearly 90 vulnerabilities patched in Microsoft’s June 2019 Security Updates. Here’s what you need to know.
Microsoft’s June 2019 Security Updates have been released, with nearly 90 vulnerabilities patched in this update, 21 of which are critical.
SandboxEscaper Privilege Escalation Bugs Patched
This month’s release contains fixes for the four local privilege escalation zero-day vulnerabilities disclosed by SandboxEscaper at the end of May 2019.
| CVE-ID | Description | Vulnerability Name |
|---|---|---|
| CVE-2019-1069 | Addresses an elevation of privilege vulnerability in the way the Task Scheduler Service validates file operations. | bearlpe |
| CVE-2019-0973 | Addresses an elevation of privilege vulnerability in the Windows Installer due to insufficient sanitization of inputs. | InstallerBypass |
| CVE-2019-1064 | Addresses an elevation of privilege vulnerability that affects how Windows AppX Deployment Service (AppXSVC) handles hard links. This vulnerability addresses the bypass of CVE-2019-0841, which was patched in the April Patch Tuesday release. | CVE-2019-0841 BYPASS |
| CVE-2019-1053 | Addresses an elevation of privilege vulnerability in Windows Shell, which impacts how it validates folder shortcuts. | Sandbox Escape in Internet Explorer 11 |
CVE-2019-0888 | ActiveX Data Objects (ADO) Remote Code Execution Vulnerability
An ActiveX vulnerability (CVE-2019-0888) was discovered that could allow an attacker to run code on the victim’s machine if said victim visited a malicious website.
If your organization blocks ActiveX objects from running in your user’s browsers, that would prevent this vulnerability from being exploited, but we always recommend applying patches ASAP.
CVE-2019-1019 | Microsoft Windows Security Feature Bypass Vulnerability
A vulnerability in the NETLOGON service (CVE-2019-1019) would allow a man-in-the-middle attack to obtain session keys from a user’s logon session, and log into the same target machine as the legitimate user.
Tenable Solutions
Users can create scans that focus specifically on our Patch Tuesday plugins. From a new advanced scan, in the plugins tab, set an advanced filter for Plugin Name Contains June 2019.
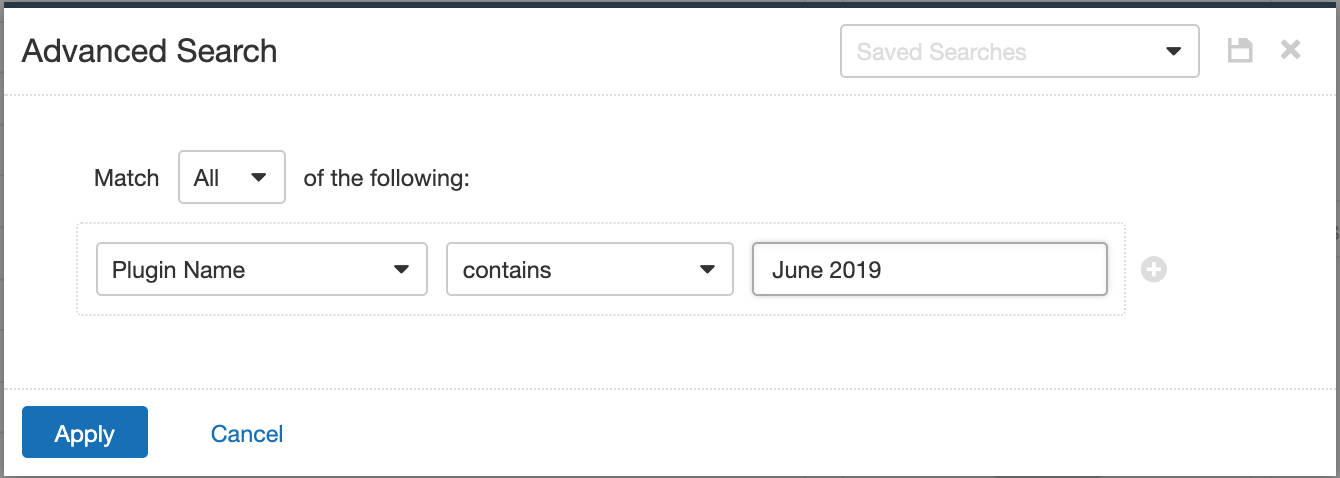
With that filter set, click on the plugin families to the left, and enable each plugin that appears on the right side. Note that if your families on the left say Enabled then that means all of the plugins in that family are set. Disable the whole family before selecting the individual plugins for this scan. Here’s an example from Tenable.io:
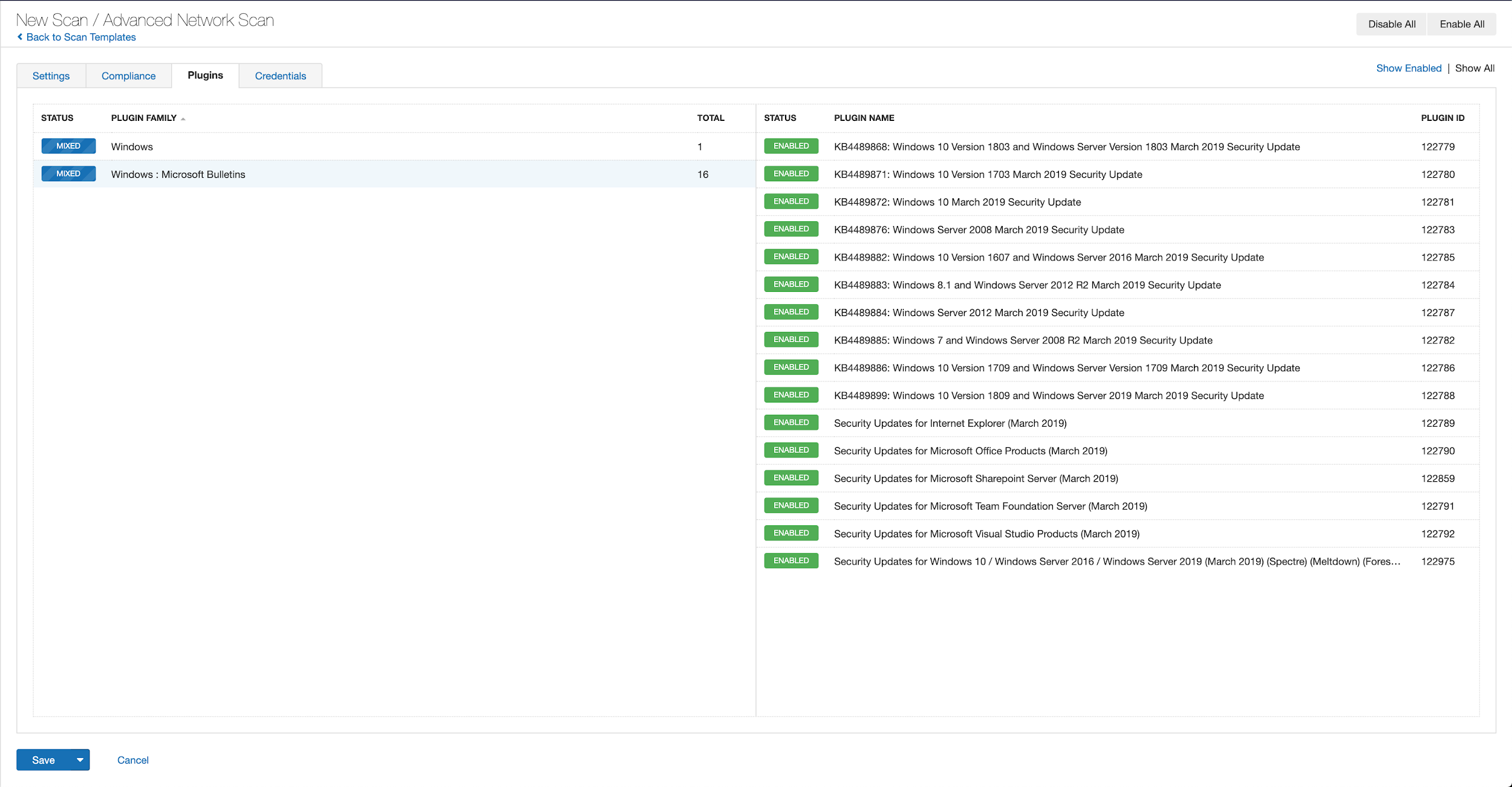
A public list of all of the plugins for Tenable’s June 2019 Patch Tuesday update can be found here as they're released.
Learn more:
- Threat Intelligence
- Threat Management
- Vulnerability Management
- Vulnerability Scanning


