CISA Releases FOCAL Plan to Help Federal Agencies Reduce Cyber Risk

CISA’s FOCAL Plan, which aims to standardize the cybersecurity operations of federal civilian agencies, marks an important step in the federal government's efforts to strengthen cyber defenses and reduce agency risk. Learn how Tenable One for Government, which recently achieved FedRAMP Authorization, aligns to the FOCAL Plan key priorities.
Each Federal Civilian Executive Branch (FCEB) agency has a unique role in supporting the mission of the U.S. federal government, from national security to healthcare to education. However, agencies’ approaches to managing cyber risk vary widely, with each agency operating independent networks with interconnected systems and varying degrees of cyber risk tolerance. This complexity makes managing exposures across the FCEB a complex challenge and drives the need for a coordinated cybersecurity strategy.
To address this issue, the Cybersecurity and Infrastructure Security Agency (CISA) recently unveiled the “Federal Civilian Executive Branch (FCEB) Operational Cybersecurity Alignment (FOCAL) Plan.” It’s designed to enhance cybersecurity across the FCEB by standardizing essential components of operational cybersecurity throughout the federal enterprise and enabling a collective defense approach. It provides actionable steps federal agencies can take, with their varied architectures and risk management strategies, to mitigate cyber risks and improve resilience through a unified approach to operational defense. And while it is not an exhaustive list of all the things agencies must do to secure their missions, it does provide a baseline for agencies to focus resources on those actions that substantially advance operational cybersecurity improvements and alignment goals.
CISA’s FOCAL Plan priority areas
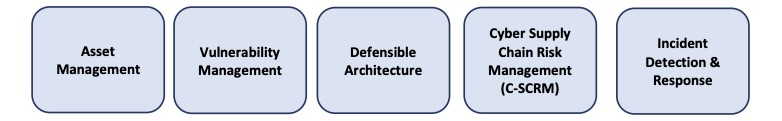
(Source: “Federal Civilian Executive Branch (FCEB) Operational Cybersecurity Alignment (FOCAL) Plan,” CISA, September 2024.)
- Asset Management
To safeguard federal networks, agencies must have comprehensive visibility into their entire infrastructure, and continuously assess how those assets are interconnected. As the old saying goes: “You can’t protect what you can’t see.” This priority area aims to ensure agencies know what assets they have so they can be properly defended.
It’s important to remember that assets span far beyond traditional IT assets. As recent mandates and CISA Binding Operational Directives (BOD) have stressed, agencies must have visibility into OT, IoT, cloud and identity assets. Look no further than the Office of Management and Budget (OMB)’s Memorandum M-24-04 which directed federal civilian departments and agencies to inventory their IoT and OT assets by the end of fiscal year 2024.
- Vulnerability Management
Getting an accurate inventory of your assets is a key first step, but it’s equally fundamental to understand the vulnerabilities on each of those assets so that you can proactively secure the attack surface. As the FOCAL Plan points out: “What constitutes an agency’s enterprise has evolved over the years, particularly as the attack surface has expanded and grown more complicated.” This has made vulnerability management more challenging. The FOCAL Plan focuses on proactive vulnerability management, so that agencies can understand their exposures by identifying, assessing and mitigating vulnerabilities across asset types, before an attacker can exploit them.
- Defensible Architecture
Because attacks are inevitable and resilience is critical, this priority area focuses on building robust, defensible infrastructures with principles like segmentation, identity management and zero-trust security. With a focus on limiting an attacker's ability to access sensitive data when a compromise occurs, this priority aims to help agencies minimize impact and operational disruptions through the implementation of proper tools and controls.
- Cyber Supply Chain Risk Management (C-SCRM)
FCEB agencies often rely on third-party vendors, which can introduce supply chain risk. This priority addresses the risk posed by external vendors and technologies by ensuring agencies can quickly identify, assess and mitigate vulnerable software and hardware from their suppliers and partners.
Case in point: the critical Log4j vulnerability, known as Log4Shell, a critical remote code execution vulnerability in Apache’s Log4j software library. This vulnerability posed a massive risk due to the widespread use of the Apache Log4j open-source logging library in many enterprise applications and cloud services, and the ease with which the vulnerability could be exploited. In the days that followed, every agency and industry security practitioner had to detect all instances of Log4j in their environment. In many cases, versions of the offering were buried deep within third-party software packages or government off-the-shelf solutions. Agencies with a complete understanding of the software deployed across their environment were able to quickly respond to the threat, and meet or exceed the deadline established by the CISA Emergency Directive (ED) 22-02. Unfortunately, Log4Shell quickly became a crisis for security teams that did not have a complete understanding of their inventory.
- Incident Detection and Response
This priority area is geared towards strengthening the ability of security operations centers (SOCs) to detect, respond to, and mitigate cyberattacks rapidly and effectively. As mentioned earlier, attacks are inevitable, so it’s critical to quickly detect and respond to an attack. Combining rapid detection and response with best practices such as segmentation and identity management will further disrupt an attacker's ability to access sensitive data.
Meeting CISA FOCAL Plan priorities with Tenable One
We’re excited to share that Tenable One is now FedRAMP authorized at the moderate impact level. Tenable One for Government is an exposure management platform designed to help agencies radically unify security visibility, insight and action across the attack surface to rapidly expose and close the gaps that put agencies at risk.
Tenable One for Government helps agencies meet CISA FOCAL Plan priorities with:
- Centralized visibility of all assets across the attack surface, from IT infrastructure to cloud environments to critical infrastructure, containers, identity systems, web applications and everywhere in between.
- Vulnerability enumeration and prioritization so you can pinpoint priority weaknesses and focus on the actual exposures that matter to quickly reduce cyber risk.
- A defensible architecture based on zero trust principles so you can quickly detect and respond to attacks in real time, map attack paths and surface all the possible steps that attackers could take to move laterally, escalate privileges and gain control of your infrastructure.
- A deep understanding of overall cyber risk with risk metrics and exposure scores to easily identify problem areas across your agency infrastructure. You can then set precise, trackable KPIs and SLAs to hold teams accountable for managing risk.
Learn more:
- Exposure Management
- Exposure Management
- Federal
- Government


