CVE-2025-0282: Ivanti Connect Secure Zero-Day Vulnerability Exploited In The Wild

Ivanti disclosed two vulnerabilities in its Connect Secure, Policy Secure and Neurons for ZTA gateway devices, including one flaw that was exploited in the wild as a zero-day.
Update January 16: The Proof-of-concept section has been updated to highlight the availability of a public proof-of-concept exploit for CVE-2025-0282.
Background
On January 8, Ivanti published a security advisory for two vulnerabilities affecting multiple products including Ivanti Connect Secure, Ivanti Policy Secure and Ivanti Neurons for Zero Trust Access (ZTA) gateways:
| CVE | Description | CVSSv3 |
|---|---|---|
| CVE-2025-0282 | Ivanti Connect Secure, Ivanti Policy Secure and Ivanti Neurons for ZTA gateways Stack-based Buffer Overflow Vulnerability | 9.0 |
| CVE-2025-0283 | Ivanti Connect Secure, Ivanti Policy Secure and Ivanti Neurons for ZTA gateways Stack-based Buffer Overflow Vulnerability | 7.0 |
Analysis
CVE-2025-0282 is a stack-based buffer overflow vulnerability in Ivanti Connect Secure, Ivanti Policy Secure and Ivanti Neurons for ZTA gateways. An unauthenticated, remote attacker that successfully exploits this flaw would obtain remote code execution on a vulnerable device.
CVE-2025-0283 is also a stack-based buffer overflow in Ivanti Connect Secure, Ivanti Policy Secure and Ivanti Neurons for ZTA gateways. Unlike CVE-2025-0282, a local, authenticated attacker that successfully exploits this flaw would be able to elevate privileges on a vulnerable device.
In-the-wild exploitation observed for CVE-2025-0282
In a blog post, Ivanti confirmed that they have observed in-the-wild exploitation of CVE-2025-0282 in “a limited number of customers” of Ivanti Connect Secure devices. They reiterate that they have not observed exploitation against Ivanti Policy Secure or Neurons for ZTA gateways.
On-going investigation reveals preliminary insight into malicious activity
On January 8, researchers at Google Mandiant published a blog post outlining their preliminary findings related to the in-the-wild exploitation of CVE-2025-0282. While the researchers have yet to link the attacks to any particular advanced persistent threat (APT) group or cluster, they have identified several malware samples on compromised systems, including the SPAWN ecosystem of malware (e.g. SPAWNANT, SPAWNMOLE and PAWNSNAIL) as well as newly discovered malware such as a credential harvesting tool called DRYHOOK and a dropper called PHASEJAM. For more information, please visit the Google Mandiant blog.
Historical exploitation of Ivanti Connect Secure
Ivanti Connect Secure, formerly known as Pulse Connect Secure, has been frequently targeted by attackers of all types, including advanced persistent threat (APT) groups as well as ransomware affiliates and opportunistic cybercriminals.
| CVE | Description | Tenable Publications | Year |
|---|---|---|---|
| CVE-2019-11510 | Ivanti Pulse Connect Secure Arbitrary File Read Vulnerability | 1, 2, 3, 4, 5 | 2019 |
| CVE-2019-11539 | Ivanti Pulse Connect Secure and Policy Secure Command Injection Vulnerability | 1, 2, 3, 4 | 2019 |
| CVE-2020-8218 | Ivanti Pulse Connect Secure Code Injection Vulnerability | Tenable 2020 Threat Landscape Retrospective | 2020 |
| CVE-2020-8243 | Ivanti Pulse Connect Secure Code Injection Vulnerability | 1, 2 | 2020 |
| CVE-2020-8260 | Ivanti Pulse Connect Secure Unrestricted File Upload Vulnerability | 1, 2 | 2020 |
| CVE-2021-22893 | Ivanti Pulse Connect Secure Authentication Bypass Vulnerability | 1, 2 | 2021 |
| CVE-2021-22894 | Ivanti Pulse Connect Secure Buffer Overflow Vulnerability | CVE-2021-22893: Zero-Day Vulnerability in Pulse Connect Secure Exploited in the Wild | 2021 |
| CVE-2021-22899 | Ivanti Pulse Connect Secure Command Injection Vulnerability | CVE-2021-22893: Zero-Day Vulnerability in Pulse Connect Secure Exploited in the Wild | 2021 |
| CVE-2021-22900 | Ivanti Pulse Connect Secure Multiple Unrestricted Uploads Vulnerability | CVE-2021-22893: Zero-Day Vulnerability in Pulse Connect Secure Exploited in the Wild | 2021 |
| CVE-2023-46805 | Ivanti Connect Secure and Ivanti Policy Secure Authentication Bypass Vulnerability | 1, 2 | 2024 |
| CVE-2024-21887 | Ivanti Connect Secure and Ivanti Policy Secure Command Injection Vulnerability | 1, 2 | 2024 |
| CVE-2024-21893 | Ivanti Connect Secure, Policy Secure, and Neurons Server-Side Request Forgery (SSRF) Vulnerability | CVE-2023-46805, CVE-2024-21887, CVE-2024-21888 and CVE-2024-21893: Frequently Asked Questions for Vulnerabilities in Ivanti Connect Secure and Policy Secure Gateways | 2024 |
Because of the historical exploitation of these devices, customers are strongly advised to apply the available patch for these flaws as soon as possible.
Proof of concept
On January 16, researchers at watchTowr released a public proof-of-concept (PoC) exploit for CVE-2025-0282 on GitHub. The GitHub repository notes that the PoC is "broken in non-trivial ways" adding that it will "require effort to work." It also points to watchTowr's technical write-up, Exploitation Walkthrough and Techniques - Ivanti Connect Secure RCE (CVE-2025-0282) on its blog.
Solution
Ivanti has released the following patches for Connect Secure, Policy Secure and Neurons for ZTA Gateways.
| Affected Product | Affected Versions (CVE-2025-0282) | Affected Versions (CVE-2025-0283) | Fixed Version |
|---|---|---|---|
| Ivanti Connect Secure | 22.7R2 through 22.7R2.4 | 22.7R2.4 and below 9.1R18.9 and below | 22.7R2.5 |
| Ivanti Policy Secure | 22.7R1 through 22.7R1.2 | 22.7R1.2 and below | Unavailable until January 21 |
| Ivanti Neurons for ZTA gateways | 22.7R2 through 22.7R2.3 | 22.7R2.3 and below | 22.7R2.5 (Unavailable until January 21) |
Ivanti customers can utilize its Integrity Checker Tool (ICT) to identify exploitation of CVE-2025-0282.
For Connect Secure customers, Ivanti recommends performing a factory reset of devices prior to upgrading to version 22.7R2.5 “out of an abundance of caution” for those with clean ICT scan results and to “ensure any malware is removed” where ICT results “show signs of compromise.”
Identifying affected systems
A list of Tenable plugins for these vulnerabilities can be found on the individual CVE pages for CVE-2025-0282 and CVE-2025-0283 as they’re released. These links will display all available plugins for these vulnerabilities, including upcoming plugins in our Plugins Pipeline.
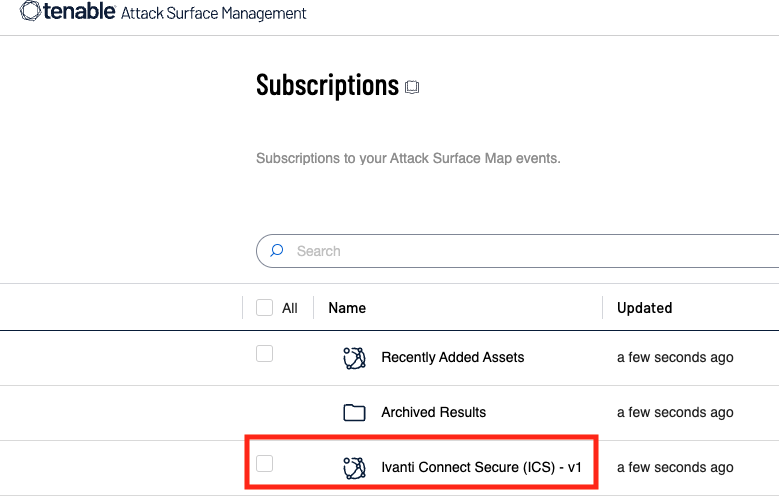
Tenable Attack Surface Management customers are able to quickly identify these assets by leveraging the built in subscription labeled Ivanti Connect Secure (ICS) - v1.
Get more information
- Security Advisory Ivanti Connect Secure, Policy Secure & ZTA Gateways (CVE-2025-0282, CVE-2025-0283)
- Security Update: Ivanti Connect Secure, Policy Secure and Neurons for ZTA Gateways
Change Log
Update January 16: The Proof-of-concept section has been updated to highlight the availability of a public proof-of-concept exploit for CVE-2025-0282.
Update January 9: The Analysis section has been updated to include preliminary details from Mandiant's on-going investigation into these attacks.
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable One, the Exposure Management Platform for the modern attack surface.
- Exposure Management
- Vulnerability Management
- Exposure Management


