Everybody Does Good Vulnerability Management When S#*t Hits the Fan

Ever notice how security teams operate more efficiently during a crisis? We need to take the same approach to security all the time. To help you get started, here are four best practices — and a new Tenable.io feature.
Have you noticed that the efficiency of security teams skyrockets in times of crisis? Take Log4j for example. The entire team drops everything to patch and minimize risk. There’s no time for debating the severity of the vulnerability or for meetings or for change reviews. Tasks are quickly coordinated, goals are established and work is done with urgency to minimize any potential impact. You’re backed up by the entire organization, and in many cases, the entire organization now suddenly has a shared common goal.
Why is it that you can’t take the same approach to security at other times? Not the panic or knee-jerk reactions. Instead, why don’t you always have shared goals? Why doesn’t your leadership always share in the goal of all other critical Tenable Vulnerability Priority Rating (VPR) vulnerabilities? (Here’s a full discussion about the disconnect between business and cybersecurity.) Why are we still debating the severity or potential impacts of critical, disclosed vulnerabilities in our environments? If we want to have an effective vulnerability management program you have to become less reactive and build a common set of policies and procedures. Doing so will allow your organization to grow and mature its program. Tenable has published several articles about how you can accomplish some of that here and here.
In this blog, we’ll share four best practices for a successful vulnerability management program, and detail a new feature in Tenable.io that will allow our users to set better goals, as well as track progress when the next headline vulnerability gets a logo or even a theme song.
Don’t get caught with a flat
We’ve all been there. We’re happily driving along on our way to meet friends, and then, out of nowhere, you get a flat tire. The time and effort needed to fix the problem may ruin your day’s plans. But tires are crucial to driving, so what do we do? We drop everything, make the flat tire a top priority and fix the problem.
Can we ensure we’ll never get a flat tire again? No. But to reduce the likelihood of it happening, we perform regular maintenance on our tires. We rotate the tires, make sure they’re properly inflated, patch them if needed and avoid construction zones littered with nails. We know the process to maintain our tires so that next time we reduce the risk of having another fun day ruined.
These same principles hold true with vulnerability management. When a major vulnerability is disclosed, you work quickly to address it. You stop everything, run targeted scans, find assets with the vulnerability and work together to patch. But unlike the tire scenario, that's often where you stop. You forget about the ongoing maintenance that helps prevent a crisis in the future.
Scanning often drives normal day-to-day patching. (That logic only works when the you-know-what hits the fan, and, more importantly, you know what vulnerabilities you’re looking for.) You get a list of vulnerabilities and patch your way through them. You try (always unsuccessfully) to patch all the vulnerabilities on your network.
What should you do? What maintenance is needed to help prevent a crisis in the future?
Building a successful vulnerability management program
We have four suggestions to help you start building a successful vulnerability management program.
- Base your vulnerability management program on goals. Having specific and stated goals for your vulnerability management program, and knowing how you will measure and present them, is critical. The goal might be related to risk or threat management, or it could be a goal to keep security patch auditing at a certain level or both. A goal helps everyone who is part of the vulnerability management program understand the purpose of the program.
- Have a strategy that defines success. The strategy for success is very much about the “hows”: how often do you scan, how often do you report, and how do you prioritize? Having a well-defined process that is agreed upon by all stakeholders ensures the security team knows how they’ll be measured so they can focus and prioritize tasks.
- Move from being reactive to proactive. Vulnerability management should be about making informed decisions, and proactively prioritizing which vulnerabilities to fix first based on the degree of risk to your organization. You need a continuous view of critical vulnerabilities on your network, what assets the vulnerabilities are on, and the likelihood that the vulnerability will be exploited. Then, you can proactively patch high-risk vulnerabilities first.
- Know where vulnerability management fits in. A strong vulnerability management program is not a one-and-done type of actively. So many other IT and security solutions are projects: deploy a new firewall, set up Virtual Private Networks (VPNs), and move to the cloud (well that one is likely never done) — you get the point. The most successful programs treat scanning as an audit of the effectiveness of people, processes and technology — finding gaps, errors and areas to improve. For example, scanning does not tell you what to patch. Your patching solutions do that work. Scans tell you what did not get patched. As a best practice, you should use other technologies to identify what patches are available in your environment, and then use vulnerability management to identify gaps between other technologies and scans.
Tenable.io remediation
To help you move your vulnerability management program from reactive to proactive, Tenable is excited to announce a new capability in Tenable.io to drive your maintenance program and help you define goals and proactively work towards success. And, when needed, better track the next time a vulnerability gets a logo or a theme song.
Remediation goals
Remediation goals help move your vulnerability management program from reactive to proactive. Using filters and tags you create ongoing program goals, assign them to individuals or teams and measure success against the goals. If your goal is to patch all vulnerabilities with a VPR of 8+ within 30 days, you’ll get a continuously updated report showing your progress toward the goal and helping you measure success.
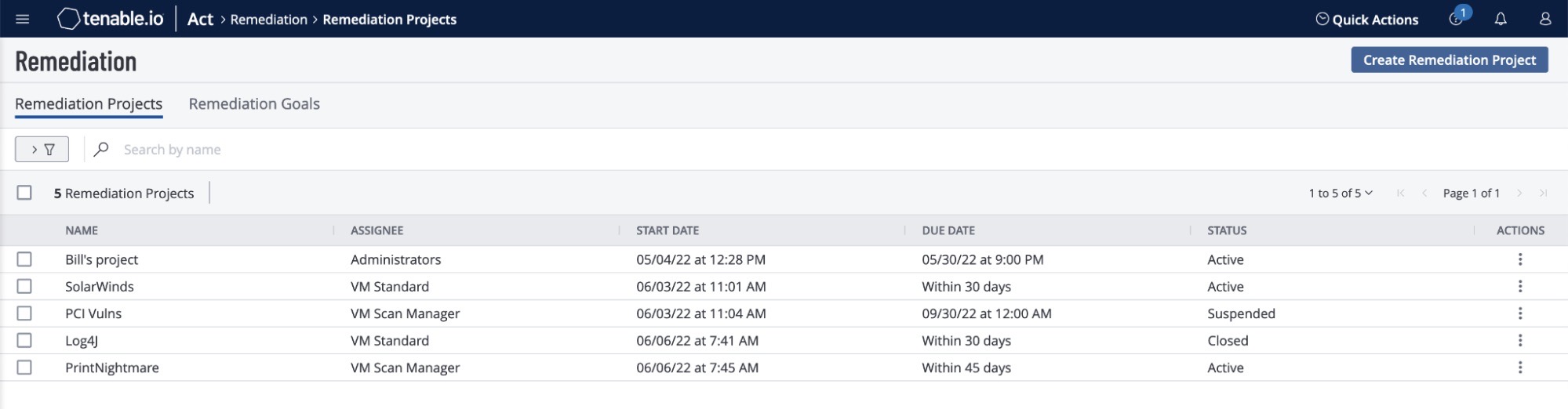
Remediation projects
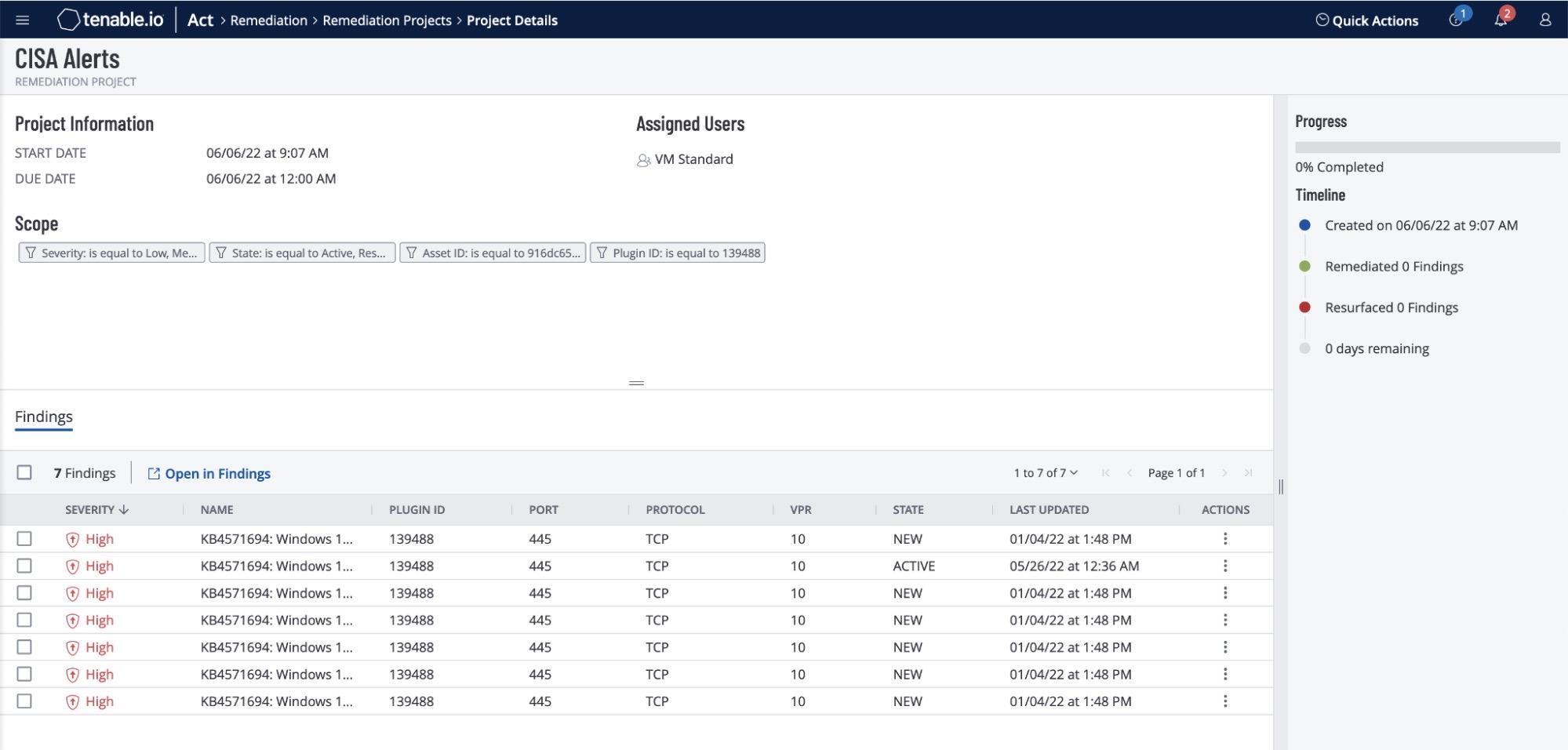
Remediation projects help you achieve project-based goals when a situation arises. Using filters and tags, you define the work, determine the scope (fixed or ongoing), assign the project to an individual or team, and track completion. For example, a tactical fixed project would include patching all Log4j vulnerabilities within five days. Once patched, the project is completed. Alternatively, you could track ongoing projects. For example, to help maintain your vulnerability management program you could ensure that present and future critical Payment Card Industry (PCI) vulnerabilities are continuously assigned to the proper people and are remediated.
Conclusion
Building a vulnerability management program can be a challenge if you’re constantly reacting to the next crisis instead of focusing on the program as a whole. While, like the tire, no amount of maintenance will always prevent a flat, building a vulnerability management program with concrete goals is the best way to enhance cyber hygiene and proactively prevent s#*t from hitting the fan.
Let Tenable help you change the tire and make sure you have a strong maintenance program. For more information view Remediation in the Tenable.io User Guide.
- Risk-based Vulnerability Management
- Tenable Vulnerability Management (DO NOT USE)
- Vulnerability Management

