Microsoft’s December 2024 Patch Tuesday Addresses 70 CVEs (CVE-2024-49138)

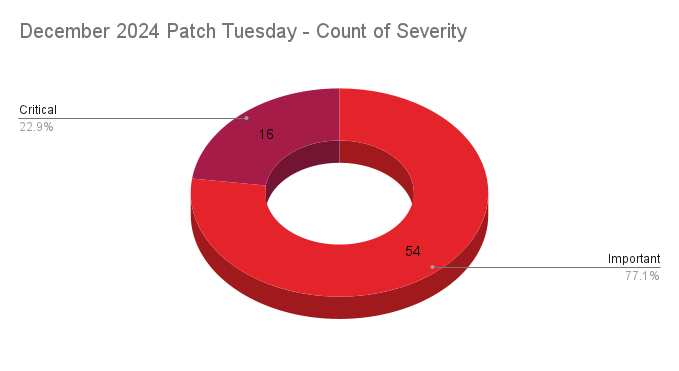
- 16Critical
- 54Important
- 0Moderate
- 0Low
Microsoft addresses 70 CVEs with 16 rated critical, including one zero-day that was exploited in the wild.
Microsoft patched 70 CVEs in its December 2024 Patch Tuesday release, with 16 rated critical, and 54 rated as important.
This month’s update includes patches for:
- GitHub
- Microsoft Defender for Endpoint
- Microsoft Office
- Microsoft Office Access
- Microsoft Office Excel
- Microsoft Office Publisher
- Microsoft Office SharePoint
- Microsoft Office Word
- Remote Desktop Client
- Role: DNS Server
- Role: Windows Hyper-V
- System Center Operations Manager
- Windows Cloud Files Mini Filter Driver
- Windows Common Log File System Driver
- Windows File Explorer
- Windows IP Routing Management Snapin
- Windows Kernel
- Windows Kernel-Mode Drivers
- Windows LDAP - Lightweight Directory Access Protocol
- Windows Local Security Authority Subsystem Service (LSASS)
- Windows Message Queuing
- Windows Mobile Broadband
- Windows PrintWorkflowUserSvc
- Windows Remote Desktop
- Windows Remote Desktop Services
- Windows Resilient File System (ReFS)
- Windows Routing and Remote Access Service (RRAS)
- Windows Task Scheduler
- Windows Virtualization-Based Security (VBS) Enclave
- Windows Wireless Wide Area Network Service
- WmsRepair Service
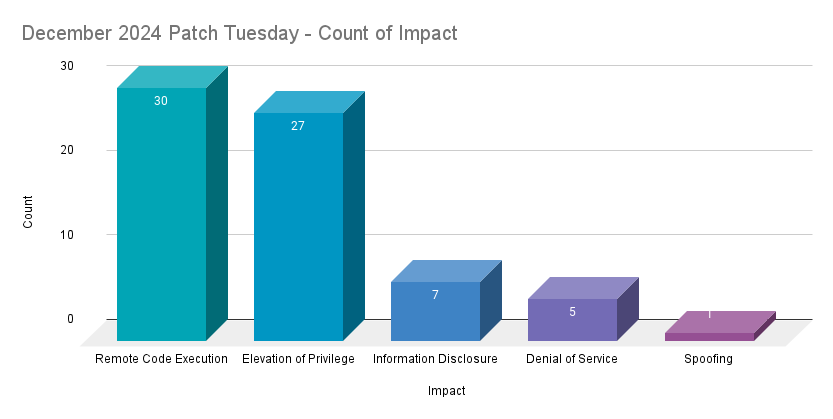
Remote code execution (RCE) vulnerabilities accounted for 42.9% of the vulnerabilities patched this month, followed by elevation of privilege (EoP) vulnerabilities at 38.6%.
CVE-2024-49138 | Windows Common Log File System Driver Elevation of Privilege Vulnerability
CVE-2024-49138 is an EoP vulnerability in the Windows Common Log File System (CLFS) Driver. It was assigned a CVSSv3 score of 7.8 and is rated as important. It was exploited in the wild as a zero-day, though no details about the in-the-wild exploitation were known at the time this blog post was published.
In addition to CVE-2024-49138, Microsoft patched two other CLFS driver EoP vulnerabilities: CVE-2024-49090, CVE-2024-49088, both assigned a CVSSv3 score of 7.8, were rated as important and assessed as “Exploitation More Likely” according to Microsoft’s Exploitability Index.
This is the ninth vulnerability in the Windows CLFS driver patched in 2024, and the first that was exploited in the wild as a zero-day this year. In 2023, there were 10 CLFS vulnerabilities patched, including two zero-day vulnerabilities in the CLFS driver that were exploited (CVE-2023-28252, CVE-2023-23376). CLFS driver vulnerabilities have been a popular attack vector and exploited in the wild by ransomware operators in the last few years according to researchers.
CVE-2024-49070 | Microsoft SharePoint Remote Code Execution Vulnerability
CVE-2024-49070 is a RCE vulnerability in Microsoft SharePoint. It was assigned a CVSSv3 score of 7.4 and is rated as important. Microsoft’s advisory notes that complexity is high and successful exploitation requires the attacker to first prepare the target in order to improve reliability of an exploit. While no details have been provided, Microsoft assessed this vulnerability as “Exploitation More Likely.”
In addition to CVE-2024-49070, Microsoft patched two information disclosure vulnerabilities (CVE-2024-49062, CVE-2024-49064) and an EoP vulnerability (CVE-2024-49068) in Microsoft SharePoint.
CVE-2024-49118, CVE-2024-49122 | Microsoft Message Queuing (MSMQ) Remote Code Execution Vulnerability
CVE-2024-49118 and CVE-2024-49122 are RCE vulnerabilities in Microsoft Message Queuing (MSMQ). Both were assigned a CVSSv3 score of 8.1 and are rated as critical. According to both of the Microsoft advisories, successful exploitation requires an attacker winning a race condition. Despite this requirement, Microsoft assessed CVE-2024-49122 as “Exploitation More Likely” while CVE-2024-49118 was assessed as “Exploitation Less Likely” as the winning the race condition must occur “during the execution of a specific operation that recurs in a low frequency on the target system.”
In order for a system to be vulnerable, the MSMQ service must be added and enabled. According to Microsoft, if the service is enabled on a Windows installation, a service named “Message Queueing” will be running on TCP port 1801. Tenable customers can use Plugin ID 174933 to identify systems that have this service running.
CVE-2024-49118 and CVE-2024-49122 brings the total to six RCE’s affecting MSMQ that were patched in 2024. One was addressed in the June Patch Tuesday (CVE-2024-30080) release, two addressed in the April Patch Tuesday (CVE-2024-26232, CVE-2024-26208) release and one in February's Patch Tuesday (CVE-2024-21363) release.
CVE-2024-49106, CVE-2024-49108, CVE-2024-49115, CVE-2024-49116, CVE-2024-49119, CVE-2024-49120, CVE-2024-49123, CVE-2024-49128 and CVE-2024-49132 | Windows Remote Desktop Services Remote Code Execution Vulnerability
CVE-2024-49106, CVE-2024-49108, CVE-2024-49115, CVE-2024-49116, CVE-2024-49119, CVE-2024-49120, CVE-2024-49123, CVE-2024-49128 and CVE-2024-49132 are RCE vulnerabilities affecting Windows Remote Desktop Services. All nine of these vulnerabilities were rated as critical and received CVSSv3 scores of 8.1. Successful exploitation is complex and requires an attacker to trigger a race condition in order to “create a use-after-free scenario” which could lead to arbitrary code execution. With a high complexity for exploitation, Microsoft assessed these vulnerabilities as “Exploitation Less Likely.”
In addition to these nine RCE’s, Microsoft addressed CVE-2024-49075, a DoS vulnerability affecting Remote Desktop Services.
Tenable Solutions
A list of all the plugins released for Microsoft’s December 2024 Patch Tuesday update can be found here. As always, we recommend patching systems as soon as possible and regularly scanning your environment to identify those systems yet to be patched.
For more specific guidance on best practices for vulnerability assessments, please refer to our blog post on How to Perform Efficient Vulnerability Assessments with Tenable.
Get more information
- Microsoft's December 2024 Security Updates
- Tenable plugins for Microsoft December 2024 Patch Tuesday Security Updates
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable One, the Exposure Management Platform for the modern attack surface.
- Exposure Management
- Vulnerability Management
- Exposure Management
- Vulnerability Management

