Microsoft’s February 2025 Patch Tuesday Addresses 55 CVEs (CVE-2025-21418, CVE-2025-21391)

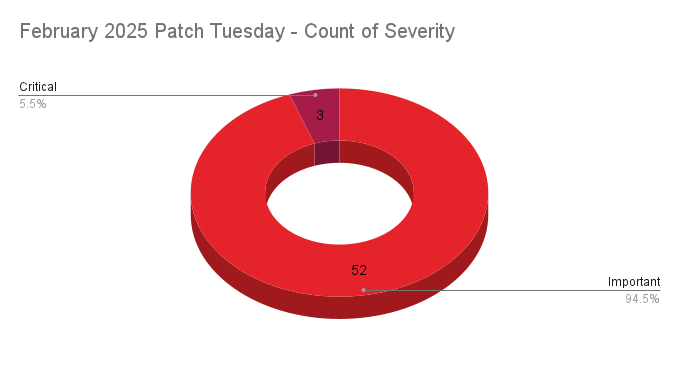
- 3Critical
- 52Important
- 0Moderate
- 0Low
Microsoft addresses 55 CVEs with three rated critical and four zero-day vulnerabilities, including two that were exploited in the wild.
Microsoft patched 55 CVEs in its February 2025 Patch Tuesday release, with three rated critical and 52 rated as important. Our counts omitted one vulnerability reported by HackerOne.
This month’s update includes patches for:
- Active Directory Domain Services
- Azure Active Directory
- Azure Firmware
- Azure Network Watcher
- Microsoft AutoUpdate (MAU)
- Microsoft Digest Authentication
- Microsoft High Performance Compute Pack (HPC) Linux Node Agent
- Microsoft Office
- Microsoft Office Excel
- Microsoft Office SharePoint
- Microsoft PC Manager
- Microsoft Streaming Service
- Microsoft Surface
- Microsoft Windows
- Outlook for Android
- Visual Studio
- Visual Studio Code
- Windows Ancillary Function Driver for WinSock
- Windows CoreMessaging
- Windows DHCP Client
- Windows DHCP Server
- Windows DWM Core Library
- Windows Disk Cleanup Tool
- Windows Installer
- Windows Internet Connection Sharing (ICS)
- Windows Kerberos
- Windows Kernel
- Windows LDAP - Lightweight Directory Access Protocol
- Windows Message Queuing
- Windows NTLM
- Windows Remote Desktop Services
- Windows Resilient File System (ReFS) Deduplication Service
- Windows Routing and Remote Access Service (RRAS)
- Windows Setup Files Cleanup
- Windows Storage
- Windows Telephony Server
- Windows Telephony Service
- Windows Update Stack
- Windows Win32 Kernel Subsystem
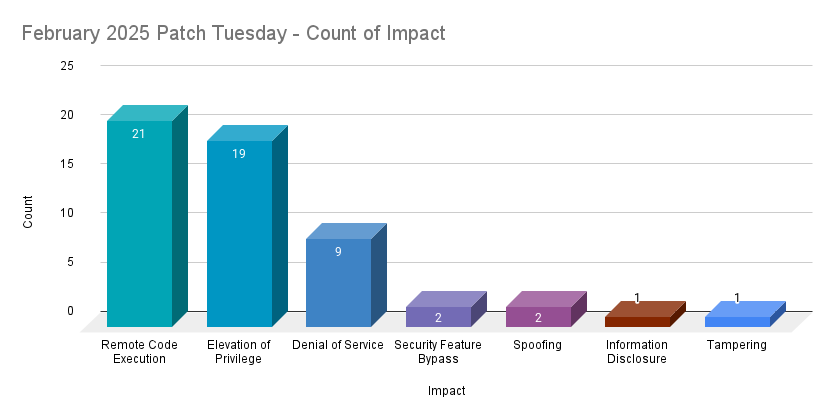
Remote code execution (RCE) vulnerabilities accounted for 38.2% of the vulnerabilities patched this month, followed by elevation of privilege (EoP) vulnerabilities at 34.5%.
CVE-2025-21418 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability
CVE-2025-21418 is an EoP vulnerability in the Ancillary Function Driver for WinSock for Microsoft Windows. It was assigned a CVSSv3 score of 7.8 and is rated important. A local, authenticated attacker could exploit this vulnerability to elevate to SYSTEM level privileges.
Microsoft notes this vulnerability was exploited in the wild as a zero-day. At the time this blog post was published, there was no other information about this exploitation.
Since 2022, there have been nine Ancillary Function Driver for WinSock EoP vulnerabilities patched across Patch Tuesday releases, including three in 2022, three in 2023, and three in 2024, including one that was exploited in the wild as a zero-day (CVE-2024-38193) by the North Korean APT known as the Lazarus Group to implant the FudModule rootkit.
CVE-2025-21391 | Windows Storage Elevation of Privilege Vulnerability
CVE-2025-21391 is an EoP vulnerability in Windows Storage. It was assigned a CVSSv3 score of 7.1 and is rated important. A local, authenticated attacker could exploit this vulnerability to delete files from a system. According to Microsoft, this vulnerability does not disclose confidential information to an attacker, rather, it only provides them with the capability to delete data, which may include data that could result in service disruption.
Microsoft notes this vulnerability was exploited in the wild as a zero-day. At the time this blog post was published, there was no other information about this exploitation.
Since 2022, there have been seven Windows Storage EoP vulnerabilities patched across Patch Tuesday releases, including two in 2022, one in 2023 and four in 2024. However, this is the first Windows Storage EoP vulnerability exploited in the wild.
CVE-2025-21194 | Microsoft Surface Security Feature Bypass Vulnerability
CVE-2025-21194 is a security feature bypass vulnerability affecting Microsoft Surface. This vulnerability was assigned a CVSSv3 score of 7.1 and was publicly disclosed prior to a patch being available from Microsoft. According to the advisory, exploitation requires multiple steps, including an attacker successfully gaining access to the same network as the device. Additionally, exploitation requires the attacker to convince the user to reboot their device. With multiple requirements for exploitation, this flaw was assessed as “Exploitation Less Likely” according to Microsoft’s Exploitability Index.
CVE-2025-21377 | NTLM Hash Disclosure Spoofing Vulnerability
CVE-2025-21377 is a New Technology LAN Manager (NTLM) Hash disclosure spoofing vulnerability that was publicly disclosed prior to a patch being made available. Despite the medium severity CVSSv3 score of 6.5, Microsoft assesses this vulnerability as “Exploitation More Likely.” Successful exploitation requires an attacker to convince a user to interact with a malicious file, such as inspecting the file or “performing an action other than opening or executing the file.” Exploitation would allow an attacker to obtain a user's NTLMv2 hash, which could then be used to authenticate as that user.
Microsoft’s advisory also notes that users that only install “Security Only” updates will also need to install Internet Explorer (IE) Cumulative updates in order to be fully protected against this vulnerability.
CVE-2025-21376 | Windows Lightweight Directory Access Protocol (LDAP) Remote Code Execution Vulnerability
CVE-2025-21376 is a critical RCE vulnerability affecting Windows Lightweight Directory Access Protocol (LDAP). This vulnerability was assigned a CVSSv3 score of 8.1, rated as critical and assessed as “Exploitation More Likely" according to Microsoft. Successful exploitation requires winning a race condition via a specially crafted request necessary to exploit a buffer overflow. If successful, the attacker could achieve RCE on an affected host.
This is the first LDAP RCE in 2025, with three having been patched in the December 2024 Patch Tuesday release, each of which were also rated as critical.
CVE-2025-21400 | Microsoft SharePoint Server Remote Code Execution Vulnerability
CVE-2025-21400 is a RCE vulnerability affecting Microsoft SharePoint Server. This vulnerability was assigned a CVSSv3 score of 8.0 and rated as important. Successful exploitation would grant an attacker the ability to execute arbitrary code. Exploitation requires an attacker to coerce the victim machine to first connect to a malicious server. This vulnerability was credited to cjm00n of Cyber Kunlun Lab and Zhiniang Peng.
CVE-2025-21184, CVE-2025-21358 and CVE-2025-21414 | Windows Core Messaging Elevation of Privileges Vulnerability
CVE-2025-21184, CVE-2025-21358 and CVE-2025-21414 are EoP vulnerabilities affecting Windows Core Messaging. Two of the three vulnerabilities were assigned CVSSv3 scores of 7.0, while CVE-2025-21358 was assigned a CVSSv3 score of 7.8. Exploitation of these flaws could allow an attacker to elevate their privileges to SYSTEM.
According to Microsoft, exploitation for CVE-2025-21184 and CVE-2025-21414 requires an attacker to gather information about the target as well as take additional measures to prepare a target for exploitation. Despite the differing requirements necessary for exploitation, Microsoft assesses all three of these vulnerabilities as “Exploitation More Likely.”
Tenable Solutions
A list of all the plugins released for Microsoft’s February 2025 Patch Tuesday update can be found here. As always, we recommend patching systems as soon as possible and regularly scanning your environment to identify those systems yet to be patched.
For more specific guidance on best practices for vulnerability assessments, please refer to our blog post on How to Perform Efficient Vulnerability Assessments with Tenable.
Get more information
- Microsoft's February 2025 Security Updates
- Tenable plugins for Microsoft February 2025 Patch Tuesday Security Updates
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable One, the Exposure Management Platform for the modern attack surface.
- Exposure Management
- Vulnerability Management
- Exposure Management
- Vulnerability Management

