New WordPress Privilege Escalation Flaw In WP GDPR Compliance Plugin

A privilege escalation flaw in WordPress’ popular WP GDPR Compliance plugin has led to exploitation of numerous WordPress sites. Site owners and administrators are encouraged to upgrade to the latest version of the affected plugin.
Background
WordPress plugin "WP GDPR Compliance" versions before 1.4.3 are vulnerable to a privilege escalation attack. The attack doesn’t require authentication, and Sucuri.net reports that attackers have already exploited a number of sites. Exploited sites had their siteurls changed to "hxxp://erealitatea[.]net".
Impact assessment
As of Noon ET on November 12, a curated Google search shows approximately 7,600 sites with changed URLs to 'erealitatea[.]net'. The malicious site seems to have been taken down, but when administrators and users attempt to interact with their Wordpress sites, most of the sites will completely fail to load or crash when administrators attempt to edit.
Vulnerability details
The affected plugin normally handles access and delete requests that are required for GDPR compliance, but versions of this plugin before 1.4.3 don’t properly sanitize the 'save_setting' action. Because of that, an attacker can inject arbitrary commands, which get stored until the plugin reaches its 'do_action()' call.
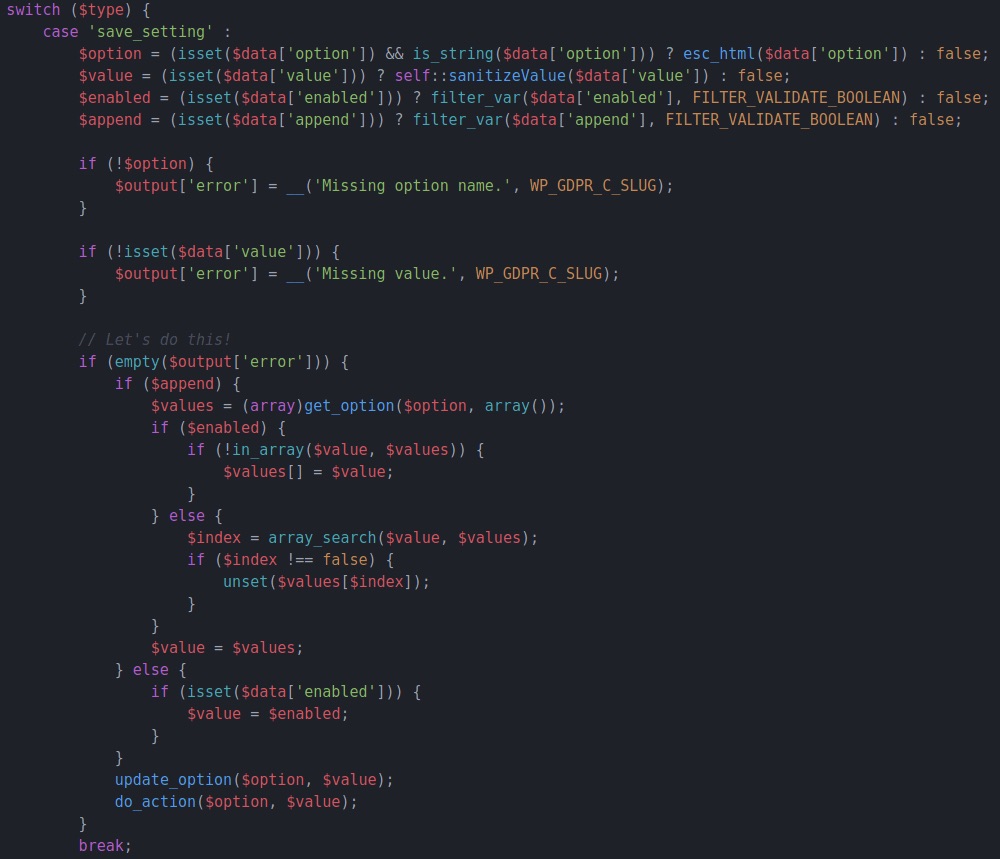
Source: Wordfence.
With these flaws, an attacker can gain administrative access to the site and make direct changes, including uploading malicious plugins for additional attacks.
Urgently required actions
Administrators can manually edit the site’s database table wp_options to fix the URL if they’ve been attacked. The record option_name contains the “siteurl“ value. Admins can modify the domain in the option_value field.
With the URL fixed, the site should load normally, but we highly recommend checking for any malicious changes or uploads to the site, or restoring the site from an uncompromised backup. Once that step has been performed, site admins should immediately update the affected plugin to the latest version.
Identifying affected systems
Plugin 101841 will detect any WordPress plugins that are out of date, which includes the WP GDPR plugin, but doesn’t reflect the criticality of this specific issue.
A list of Tenable plugins to identify this vulnerability can be found here.
Get more information
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface. Get a free 60-day trial of Tenable.io Vulnerability Management.
- Vulnerability Management
- Vulnerability Scanning


