by Cody Dumont
August 12, 2020
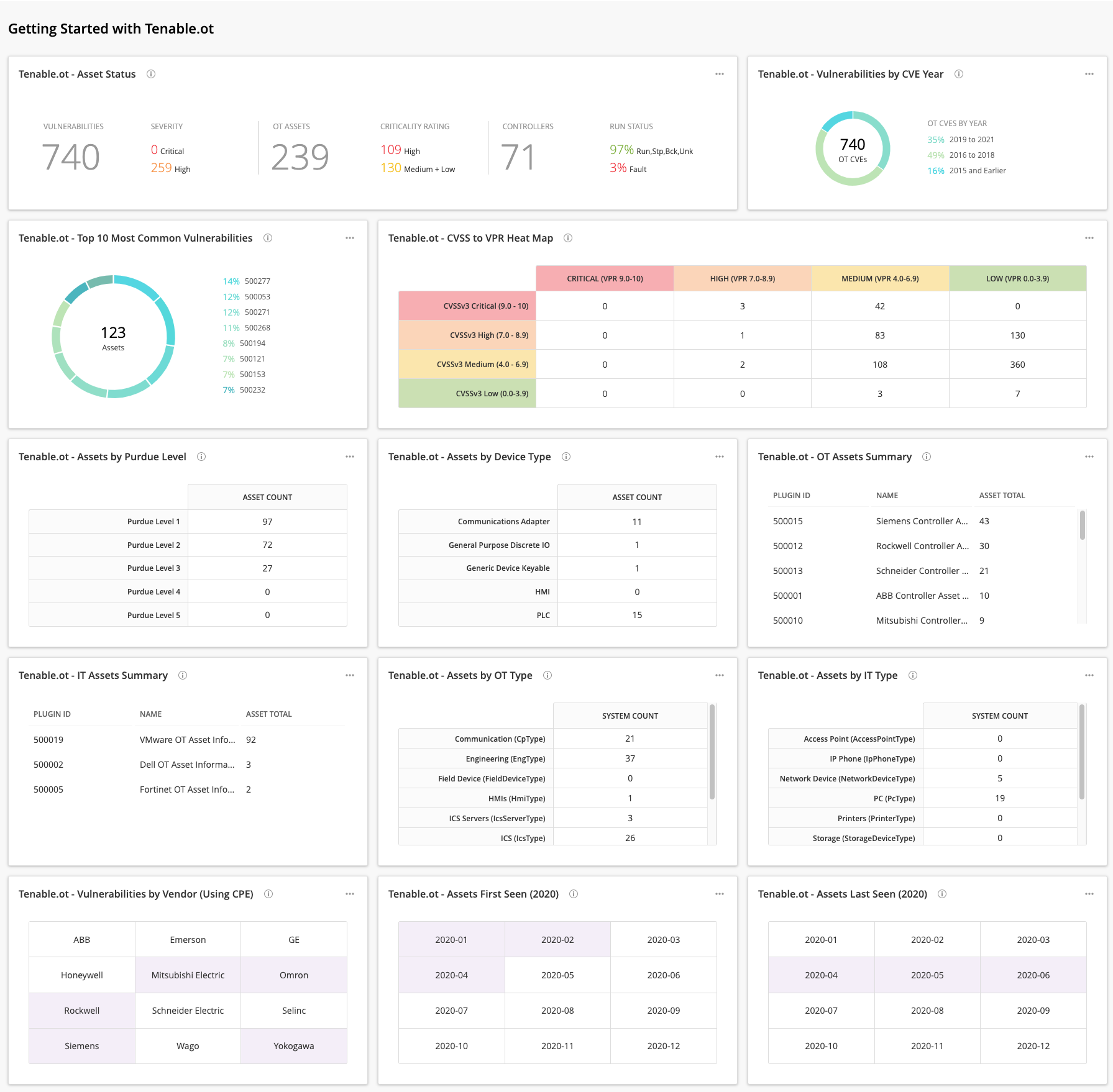
As networks converge between Information Technology (IT) and Operational Technology (OT), organizations struggle to have complete visibility of the network. Using Tenable.ot and Tenable.io together, the complete picture of a network is visible to risk managers and CISO’s. Tenable.io is able to connect with Tenable.ot and incorporate risk scores such as Vulnerability Priority Rating (VPR) and Common Vulnerability Scoring System (CVSS) vectors to fully understand risk.
As Tenable expands into OT markets, organizations are afforded the opportunity to perform risk analysis based on OT and IT data in a single unified platform with Tenable.ot and Tenable.io. In the top row, the CISO is able to quickly see the status of OT assets by the total number of assets detected, critical and high severity vulnerabilities, and the criticality rating and run status. The criticality rating is established by default per the device type, however this rating can be modified as needed.
As the role of the risk manager expands to include OT devices, the next row of widgets presents the data in a more vulnerability management-based view. The ring chart shows the most common vulnerabilities based on the total count of affected assets, and the matrix shows a heat map view aligning CVSS and VPR. By viewing the correlation of the Risk Ratings, CVSS, VPR, and criticality rating, risk managers are able to gain clear understanding of their overall IT/OT risk.
The Cyber Exposure Lifecycle begins with the Discovery phase, where the objective is to map and identify assets across the organization. The next 2 rows of provide counts and summary lists of assets by discovery classifications, such as the Purdue Levels, Device Type, OT Type, and IT Type. The Purdue Enterprise Reference Architecture (PERA) or Purdue Model is a reference architecture that can model the enterprise in multiple layers and in multiple stages of the architectural life cycle(). Tenable provides data for levels 1 - 5 as part of the asset information plugins. The Purdue Model is used heavily in the OT space to segment the operational levels. The device type is a value collected from the device vendors, and type field is a more granular field allowing for the understanding of IT vs. OT assets. The two summary tables provide a list of assets based on the OT and IT using the plugin name, as OT assets have the key word “Controller” in the name.
The final rows provide indicators for assets that were detected monthly in 2020, along with the Common Platform Enumeration (CPE) by manufacturer. The CPE attribute is part of the vulnerability plugin and can denote hardware, applications, or operating system vulnerabilities. In addition, the CPE contains manufacturer information. System managers can use this information as a starting point for vulnerability analysis and patch management efforts.
As threats to cloud, IT, and OT are exposed, organizations that practice Cyber Exposure can use Tenable.io to reduce their Cyber Exposure gap. Tenable.ot helps to expand enterprise visibility and merge traditional Vulnerability Management (VM) practices to include IT and OT. Using the advanced reporting capabilities of Tenable.io, risk managers can import data from OT networks into a single VM platform. The OT data can then be reviewed and assessed alongside the IT VM data for a complete picture of cyber risk.
Widgets
Tenable.ot - Asset Status: This widget provides an overall status summary to the risk manager. The first column displays overall vulnerability count, and provides counts for vulnerabilities with critical and high severities. The middle column provides the criticality rating which is set by default based on the device type. However, this rating can be changed manually if needed. The last column provides the operational status of the asset.
Tenable.ot - Vulnerabilities by CVE Year: This ring chart provides vulnerability percentages based on the year the CVE was reported. The chart is dynamic in nature showing the percentage as the mouse moves around the ring. Each of the percentages is groups by year ranges, indicating the newest to the oldest, from top to bottom.
Tenable.ot - Top 10 Most Common Vulnerabilities: This ring chart shows the most common Tenable.ot vulnerabilities. The filters use the vulnerability severity: low, medium, high, and critical states, which are based on CVSS scoring. The percentages shown are the percentages of the plugins that are detected in the top 10 plugins found. The colors used do not represent a vulnerability state.
Tenable.ot - CVSS to VPR Heat Map: This matrix provides a heat map to show the alignment of the Vulnerability Priority Rating (VPR) and Common Vulnerability Scoring System (CVSS) for all vulnerabilities with plugin ID in the 500K range. The Tenable.ot plugins are defined in the 500K range and use the CVE to map to the VPR. This integration provides advanced insight into the dynamic nature of risk, based on the ongoing attack surface.
Tenable.ot - Assets by Purdue Level: The Purdue Enterprise Reference Architecture (PERA) or Purdue Model is a reference architecture that can model the enterprise in multiple layers and in multiple stages of the architectural life cycle. Tenable provides data for levels 1 - 5 as part of the asset information plugins. The Purdue Model is used heavily in the OT space to segment the operational levels. Each cell provides a count of assets by tracking the “purdueLevel : Level(1-5)” in the plugin output with in the Asset Information plugins.
Tenable.ot - Asset by Device Type: This matrix provides counts for each value in the Device Types stored in the Asset Identification plugins. The Device Type value is collected from the OT vendors and stored in the plugin. This variable is not controlled by Tenable.ot.
Tenable.ot - OT Assets Summary: Tenable.ot provides OT asset information in the plugins via the plugin name filter using the keywords “Controller Asset Summary”. This table lists which of these plugins are present on the network. The list is sorted by total plugins present and uses the plugin name filter to separate the Asset Identification plugins from the vulnerability plugins.
Tenable.ot - IT Assets Summary: Tenable.ot provides IT asset information in the plugins via Asset Summary. The IT assets do not have the word “Controller” in the plugin name, therefore this widget uses two plugin name filters, the first to remove the entries with “Controller” and then finding the remaining “Asset Information” plugins. This table lists which of these plugins are present on the network. The list is sorted by total plugins present and uses the plugin name filter to separate the Asset Identification plugins from the vulnerability plugins.
Tenable.ot - Assets by OT Type: This matrix groups the Operational Technology (OT) devices so risk managers can understand how IT and OT risk is calculated. The system count column is a count of hosts, where the defined value is present in the Asset Identification plugin.
Tenable.ot - Assets by IT Type: This matrix groups the Information Technology (IT) devices so risk managers can understand how IT and OT risk is calculated. The System Count column is a count of hosts, where the defined value is present in the Asset Identification plugin.
Tenable.ot - Vulnerabilities by CPE Type: This component identifies vulnerabilities based on the Common Platform Enumeration (CPE) string and denotes hardware, application, or operating system vulnerabilities. The CPE string for this data is different from other CPE.
Tenable.ot - Assets First Seen (2020): Tenable.ot uses the date to track the first time an asset is detected. This matrix provides indicators for every month in 2020. Each row is separated by quarter, and turns purple when a match is discovered. This date does not represent the Tenable.io “Vulnerability Discovered” date.
Tenable.ot - Assets Last Seen (2020): Tenable.ot uses the date to track the last time an asset is detected. This matrix provides indicators for every month in 2020. Each row is separated by quarter, and turns purple when a match is discovered. This date does not represent the Tenable.io “Vulnerability Last Observed” date.