by Josef Weiss
November 12, 2024
Vulnerability scanning is an essential part of maintaining a strong cybersecurity defense, minimizing risks, and ensuring regulatory compliance. Many compliance standards and frameworks require regular vulnerability scanning to ensure data protection, privacy, and overall security compliance. Furthermore vulnerability scanning reveals known vulnerabilities, such as outdated software, misconfigurations, or missing patches. While human weakness (clicking on phishing links/poor security practices) is considered the largest weakness in cybersecurity, unpatched software, and misconfigurations continue to be a significant concern to many organizations.
Traditional vulnerability scanning can consume excessive system resources, burdening system resources and impacting performance. This infrastructure strain can not only increase operational costs, but may also cause frustration among IT staff and end users alike. Scanning on a schedule, such as quarterly, monthly, or even weekly, provides a snapshot view of organizational risk at the time the scan was conducted. This snapshot of risk is many times out of date by the time action is taken, and only represents organization risk accurately at the point-in-time the vulnerability scan occurred. Systems may be vulnerable for extended periods between scans, remediation efforts, and subsequent scans.
Out-of-date vulnerability and remediation information strains organizational relationships between security and other IT teams. Patches require the launch of additional scans, in the form of remediation scans, which verify the effectiveness of the applied fix. This adds yet another layer of complexity, and time to the process. Reporting is not timely, and is dependent on successful completion of remediation scans and validation. This complex process also hinders timely and accurate vulnerability and remediation reporting to organizational management.
Frequent vulnerability scanning is key, and a proactive approach to maintaining security in dynamic IT environments. Frequent scanning helps identify and address weakness in systems, applications, and networks before they can be exploited. To solve this problem and reduce the burden that is present with traditional frequent vulnerability scanning, Tenable has released a new feature in Tenable Agent known as Continuous Assessment, which delivers continuous, ultra-lightweight scanning and provides near real-time insights. This ensures organizations are always aware of their security posture, enabling them to take immediate action. This agent maintains continuous visibility into risks, has little resource consumption, streamline workflows, and minimizes time between detection and remediation.
This dashboard utilizes information gathered from Tenable Agent’s Continuous Assessment to provide near real-time vulnerability information. Vulnerability and remediation information is provided using bothContinuous Assessment and Tenable Agent. Organizations can visualize precisely how their remediation efforts are stacking up to organizational policies. Organizations can see mitigation timeframes in hours, as opposed to days, or even weeks, without the need to launch remediation scans, and compare those to existing mitigation strategies.
Tenable provides several solutions for organizations to better understand vulnerability management. Security leaders need to SEE everything, PREDICT what matters most and ACT to address cyber risk and effectively align cybersecurity initiatives with business objectives. Tenable Vulnerability Management (formerly Tenable.io) discovers and analyzes assets continuously to provide an accurate and unified view of an organization's security posture. The requirements for this report are: Tenable Vulnerability Management.
Widgets
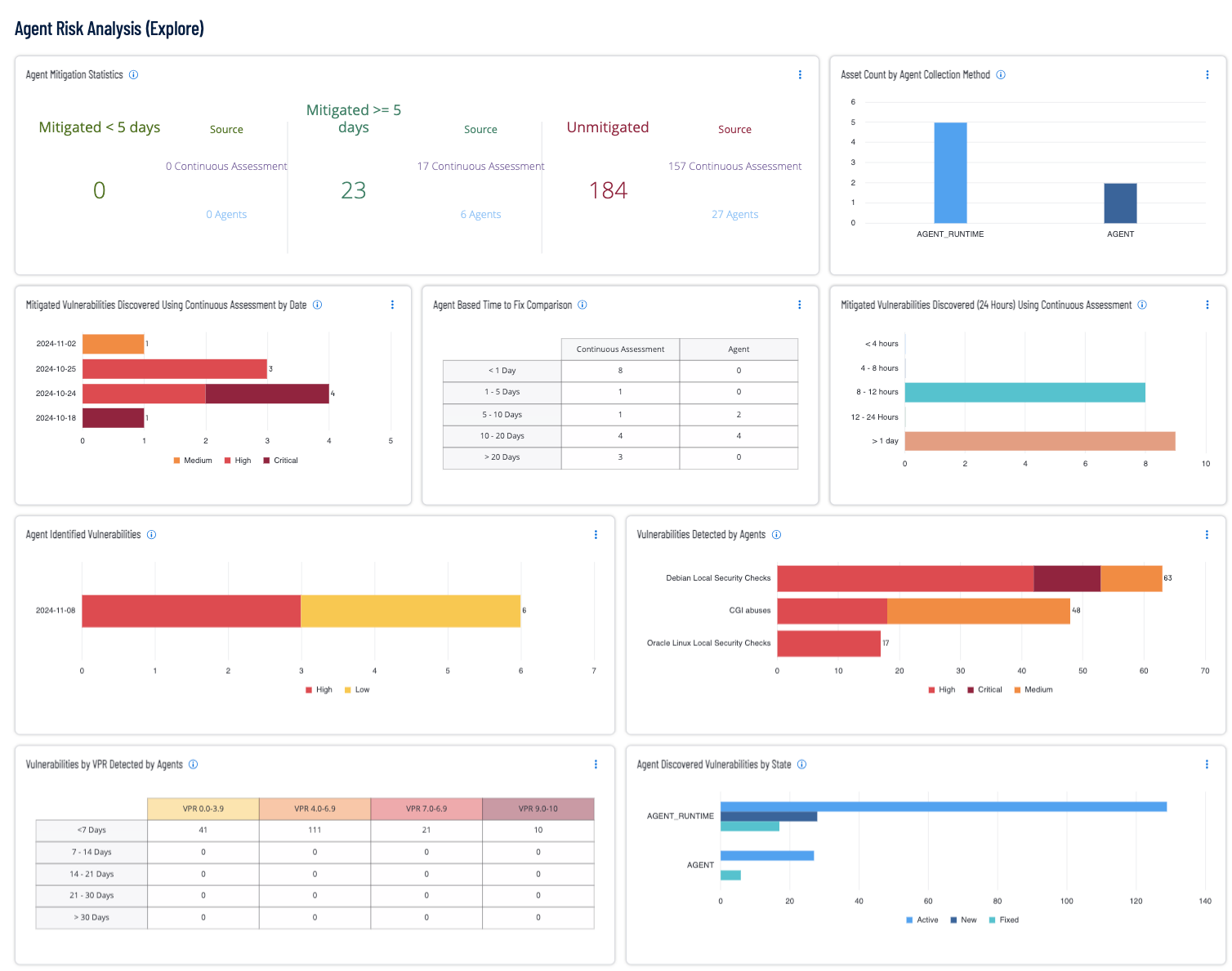
- Agent Mitigation Statistics - This widget displays the statistics of mitigated vulnerabilities between Tenable runtime agents, which provide near real-time data, and Nessus Agents.
- Asset Count by Agent Collection Method - This widget displays the count of agents that are currently active and reporting.
- Mitigated Vulnerabilities Discovered Using Continuous Assessment by Date - This widget displays the number of Critical, High, and Medium vulnerabilities that have been mitigated at a specific date and time.
- Agent Based Time to Fix Comparison - This widget displays the number of vulnerabilities that have been mitigated over time.
- Mitigated Vulnerabilities Discovered (24 Hours) Using Continuous Assessment - This widget displays remediation efforts that have been discovered in the last 24 hours on assets that have Tenable Agent Continuous Assessment enabled.
- Agent Identified Vulnerabilities - This widget displays the number of Critical, High, and Medium vulnerabilities that have been reported/identified at a specific date and time.
- Vulnerabilities Detected by Agents - This widget displays the number of Critical, High, and Medium vulnerabilities that have been reported/identified by plugin Family.
- Vulnerabilities by VPR Detected by Agents - This widget displays the number of vulnerabilities that have been reported/identified by Vulnerability Priority Rating (VPR).
- Agent Discovered Vulnerabilities by State - This widget displays vulnerabilities by state (active and fixed) by agent type.