by Josef Weiss
December 5, 2024
The proliferation of unsupported and end-of-life (EOL) products is a common security problem experienced across all organizations. As applications and operating systems reach EOL, vendors stop offering support, causing security and stability to decrease over time. This dashboard provides organizations with a clear and simplified method to identify EOL software and enables security managers to predict where risk will increase to develop a mitigation plan.
Identifying assets running EOL applications is an important part of assessing and minimizing organizational risk since patches, updates and security fixes are longer available. Many industries have regulatory requirements (e.g., GDPR, HIPPA, PCI-DSS,) that mandate up-to-date software. In addition, the Center for Internet Security (CIS) states that organizations must ensure that only software applications or operating systems that are currently supported and receiving vendor updates are added to the organization’s authorized software inventory.
Tenable Vulnerability Management enables organizations to continuously assess the health and security posture of the network, including identification and monitoring of unsupported software. Quick identification of unsupported operating systems and applications, enables risk managers to see risks associated with EOL software. Identifying exposures, provides the operations teams direction to implement, act, and prioritize remediation efforts to mitigate cyber risk. Risk managers and operations teams can communicate to the leadership team how upgrading unsupported operating systems and applications reduces their network risk.
Tenable.io uses active methods to identify EOL products found in the environment by examining the Microsoft registry, common software installation locations, or using applications utilities such as YUM or APT in Linux systems. Risk managers are able to verify the operation team's activities and identity areas for risk mitigation.
This dashboard provides the organization with a clear and simplified method to identify EOL software and enables security managers to predict where risk will increase and develop a mitigation plan.
Security leaders need to SEE everything, PREDICT what matters most and ACT to address cyber risk and effectively align cybersecurity initiatives with business objectives. Tenable.io discovers and analyzes assets continuously to provide an accurate and unified view of an organization’s security posture. The requirements for this dashboard are: The requirements for this dashboard are: Tenable Vulnerability Management (Nessus, NNM).
Widgets
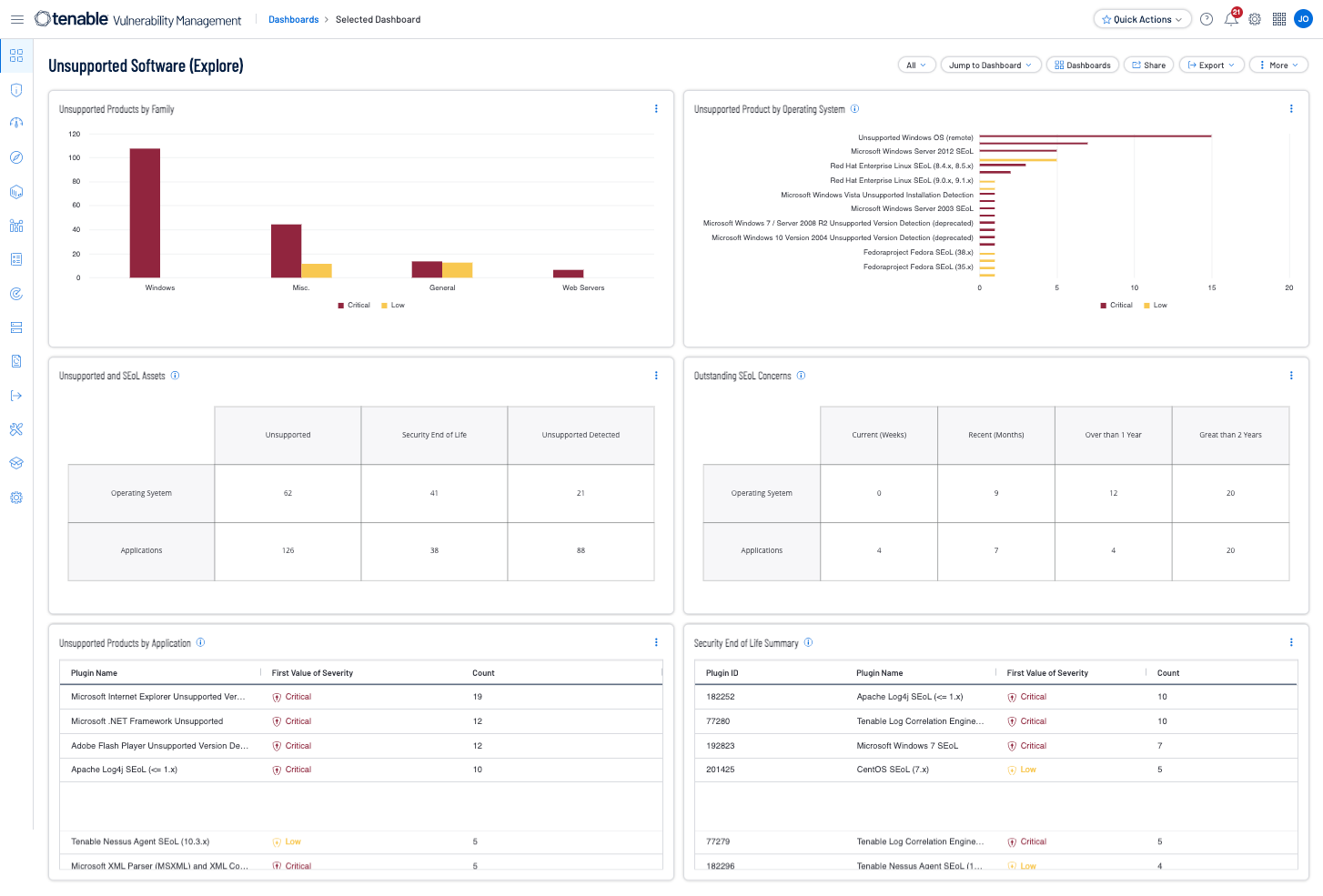
- Unsupported Products by Application - The Unsupported Applications table displays all unsupported applications by name, sorted by count.
- Unsupported Products by Operating System - The Unsupported Operating Systems chart displays all unsupported operating systems, sorted by count.
- Security End of Life Summary - The Security End of Life Summary table displays products that have entered the Security End of Life state of the Security Maintenance Lifecycle.
- Unsupported Products by Family - The Unsupported Products by Family chart displays all unsupported products, sorted by Family.
- Outstanding SEoL Concerns - The Outstanding SEoL Concerns widget displays assets counts by two categories, Operating System and Application.
- Unsupported and SEoL Assets - The Unsupported and SEoL widget displays assets counts by two categories, Operating System and Application.