by Josef Weiss
November 7, 2022
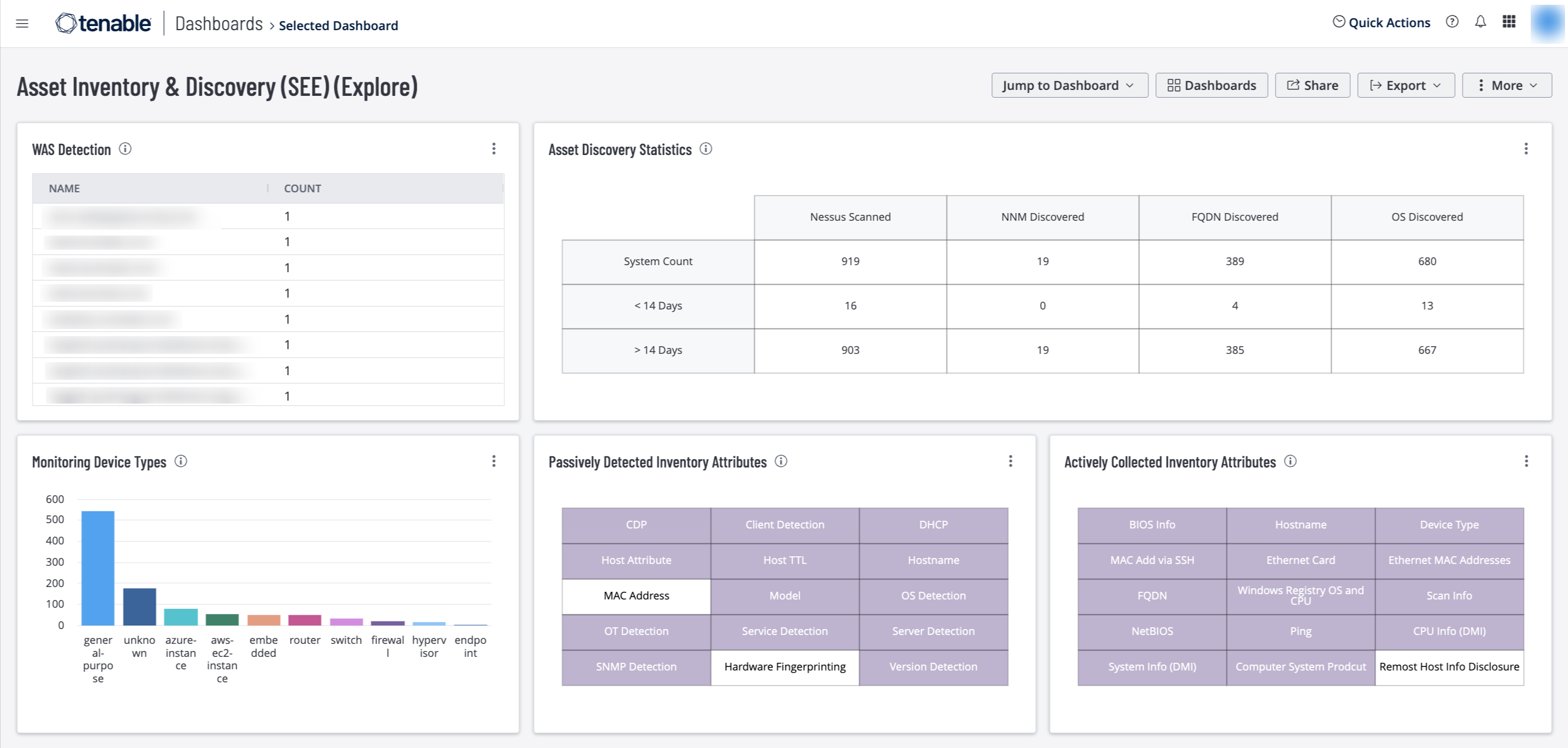
Organizations must know the existence and location of critical assets to ensure that assets are monitored and protected based on each asset’s business risk rating. Identifying assets facilitates vulnerability scanning and remediation by ensuring that scans are configured to probe for common weaknesses in the platform or application. Discovering all assets enables organizations to establish an inventory, which can be used to assess and mitigate associated risks to the organization.
Attacker vectors are global. Attackers continuously scan the address space of target organizations, looking for new and unprotected systems to be attached to the network. Maintaining a comprehensive and up-to-date asset inventory is a fundamental and critical component of Risk-Based Vulnerability Management (RBVM). Asset identification of all connected assets within an organization is a common baseline requirement in a number of security standards, such as NIST Special Publication 800-53 and General Data Protection Regulation (GDPR). Maintaining an asset inventory is also the critical first step in the Discovery phase of RBVM, allowing organizations to be more proactive.
This dashboard provides guidance to establish an asset discovery, including:
- Actively and passively detected assets
- Asset discovery statistics
- Detected web applications
- Indications for device types (printers, cameras, routers, firewalls, WAPs)
Security leaders need to SEE everything, PREDICT what matters most and ACT to address cyber risk and effectively align cybersecurity initiatives with business objectives. Tenable.io discovers and analyzes assets continuously to provide an accurate and unified view of an organization’s security posture. The requirements for this dashboard are: Tenable.io Vulnerability Management (Nessus, NNM), Tenable Web Application Security (WAS).
Widgets
Monitoring Device Types – This widget displays the top 10 device types identified within the organization. The widget utilizes the system type filter within the asset workbench to identify device types. The requirements for this widget are: Tenable.io Vulnerability Management (Nessus, NNM).
WAS Detection – This widget provides an updated list of Web Applications detected by Tenable.io WAS. When an asset name is selected, the vulnerability list and details for that web application are displayed. Developers and security teams can use this information to identify and categorize web applications. The requirement for this widget is: Tenable Web Application Security (WAS).
Asset Discovery Statistics – This widget provides a high-level view of host discovery. Each column depicts a different detection method, and each row uses the Vulnerability First Seen filter to identify when a plugin was first detected. The Vulnerability First Seen field is set when a plugin and Asset are first encountered. Analysts can leverage this widget to gain insight on how and when devices are first detected. The plugins used in this component are: - 12: Host TTL Discovered - 11936: OS Identification - 12053: Host Fully Qualified Domain Name (FQDN) Resolution - 19506: Nessus Scan Information. The requirements for this widget are: Tenable.io Vulnerability Management (Nessus, NNM).
Passively Detected Inventory Attributes – This widget displays passively collected asset attributes that can be used to build an asset inventory. When selected, each highlighted indicator provides a list of plugins with host counts, enabling analysts to review the details of each discovered attribute. The requirements for this widget are: Tenable.io Vulnerability Management (Nessus, NNM).
Actively Collected Inventory Attributes – This widget displays actively collected asset attributes that can be used to build an asset inventory. When selected, each highlighted indicator provides a list of plugins with counts, enabling analysts to review the details of each discovered attribute. The requirements for this widget are: Tenable.io Vulnerability Management (Nessus, NNM).