by Carole Fennelly
November 7, 2022
A compromised processor is one of the most serious attack vectors on any platform. The hardware bugs known as Spectre and Meltdown affect modern processors by accessing information found in the system's memory. The Spectre and Meltdown dashboard provides insight into which systems are affected by these hardware bugs.
The Spectre and Meltdown bugs use side channels to obtain information from the accessed memory location. Spectre allows an application to force another application to access arbitrary portions of its memory, which can then be read through a side channel. This unique side channel attack uses speculative execution, a technique used by high-speed processors, to increase performance by guessing likely future execution paths and preemptively executing the instructions in them. Spectre leverages this execution and affects all modern processors capable of keeping instructions in flight.
Tenable.io enables organizations to manage risk exposure by providing information on all outstanding patches for each operating system, and assigning a criticality to each vulnerability found. This information enables infrastructure and security teams to target systems that have a higher probability of being compromised.
Security leaders need to SEE everything, PREDICT what matters most and ACT to address cyber risk and effectively align cybersecurity initiatives with business objectives. Tenable.io discovers and analyzes assets continuously to provide an accurate and unified view of an organization’s security posture. The requirements for this dashboard are: Tenable.io Vulnerability Management (Nessus).
Widgets
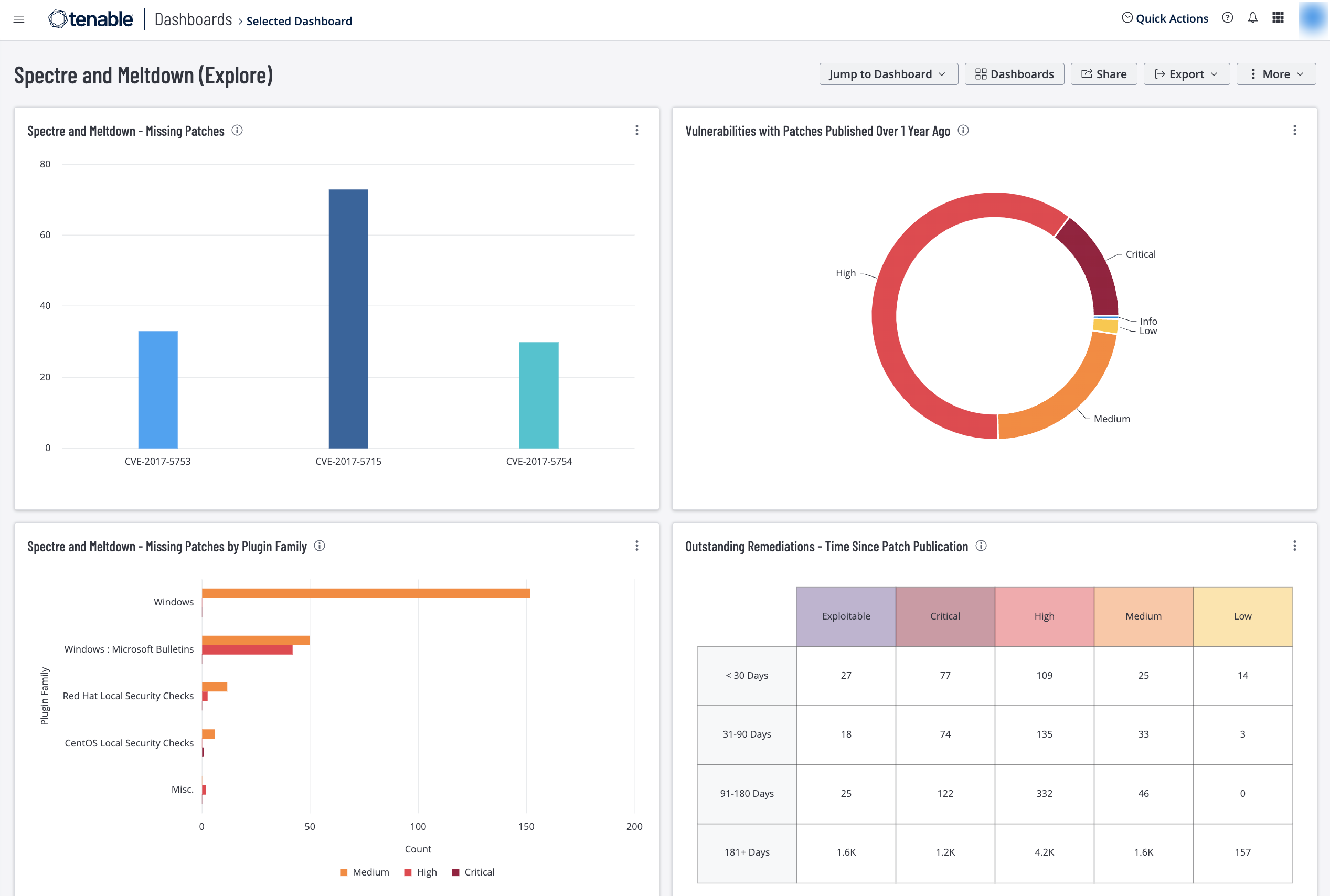
Spectre & Meltdown - Missing Patches: This widget provides a summary of the top vulnerabilities related to CVE-2017-5753, CVE-2017-5715 and CVE-2017-5754. The chart provides an overview for each CVE that has been issued related to Spectre & Meltdown and filters on patches that are available for those CVEs. This information enables analysts to remediate the vulnerabilities on affected systems and significantly reduce their exposure. The requirements for this widget are: Tenable.io Vulnerability Management (Nessus).
Spectre & Meltdown - Missing Patches by Plugin Family: This widget provides indicators by plugin family of missing patches related to CVEs 2017-5715, 2017-5753, 2017-5754 for Spectre and Meltdown. The results are grouped by Plugin Family and severity and sorted with the Plugin Family containing the most vulnerabilities at the top. The requirements for this widget are: Tenable.io Vulnerability Management (Nessus).
Vulnerabilities with Patches Published Over 1 Year Ago: This widget provides a quick snapshot of the older vulnerabilities detected in the organization. The vulnerabilities in the chart have patches that were published over one year ago. Analysts can use this chart for a quick overview to help plan vulnerability remediation or risk mitigation efforts. The requirements for this widget are: Tenable.io Vulnerability Management (Nessus).
Cyber Essentials Scheme - Vulnerabilities by Patch Published Date: This widget provides counts of vulnerabilities with patches that have been published in the specified date ranges. The date ranges are less than 7 days ago, less than 30 days ago, less than 90 days ago and more than 90 days ago. The columns in the matrix group the vulnerabilities by severity, ranging from low to critical. The low severity vulnerabilities are displayed on a green background, the medium severities on yellow, the high severities on orange and the critical severities on red. The bottom row of the matrix displays the counts of exploitable vulnerabilities with patches published more than 90 days ago. The requirements for this widget are: Tenable.io Vulnerability Management (Nessus).