by Carole Fennelly
November 3, 2022
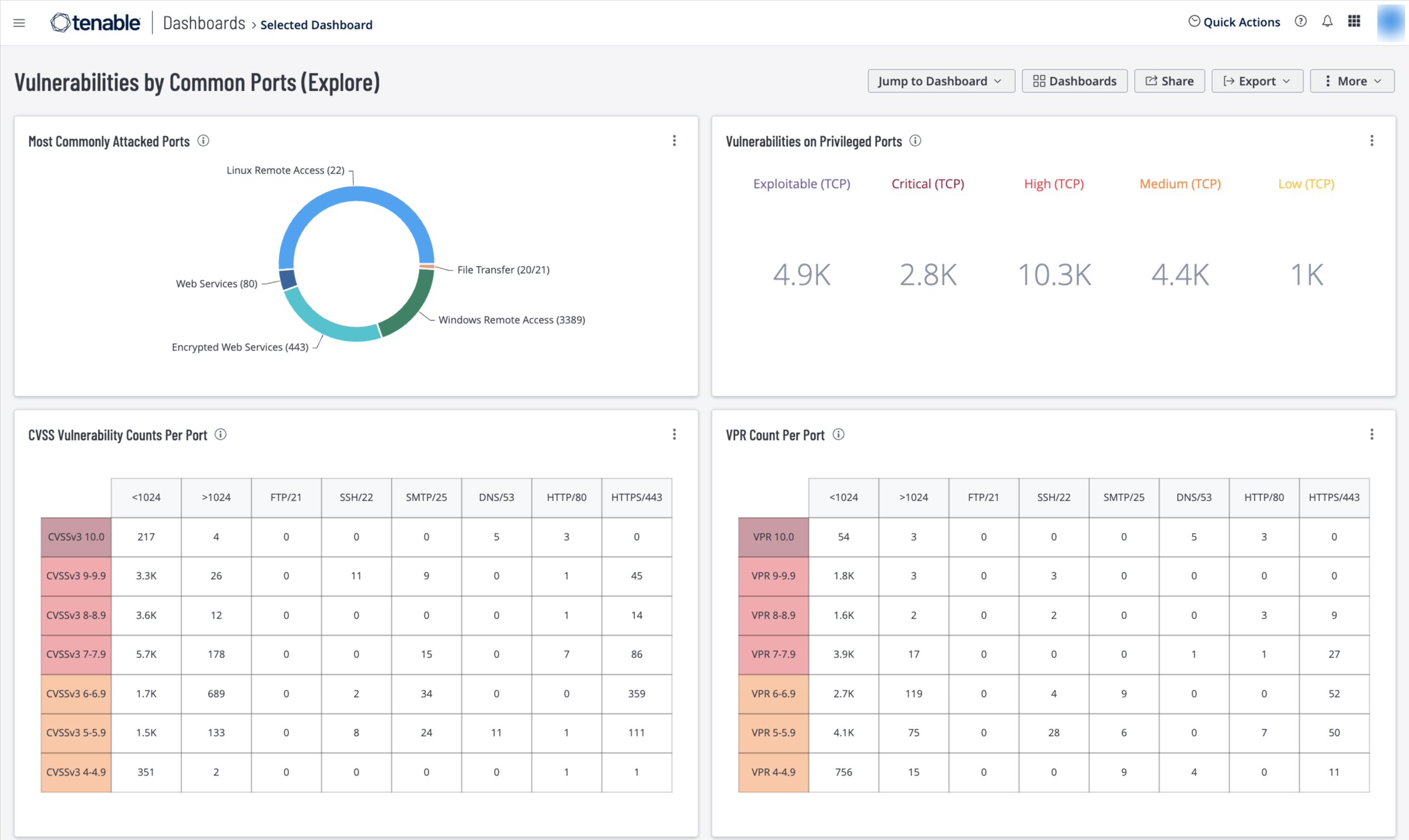
Addressing vulnerable services is a key step in reducing network risk. Vulnerable services may allow malicious actors to infiltrate the network, compromise assets, and exfiltrate information. This dashboard presents vulnerability information by common TCP ports and services identify potentially vulnerable services.
The components on this dashboard leverage a variety of active and passive port filters to display vulnerability information in multiple ways. Asset counts and vulnerability counts are presented based on specific ports, ranges of ports, and CVSS scores. Vulnerabilities that are known to be exploitable are highlighted since they are the most critical to address immediately. The vulnerability information on this dashboard can be used to remediate service vulnerabilities and improve the security of the network.
Security leaders need to SEE everything, PREDICT what matters most and ACT to address cyber risk and effectively align cybersecurity initiatives with business objectives. Tenable.io discovers and analyzes assets continuously to provide an accurate and unified view of an organization’s security posture. The requirements for this dashboard are: Tenable.io Vulnerability Management (Nessus, NNM).
Widgets
Most Commonly Attacked Ports – This widget displays the most frequently attacked ports. The greatest number of attacks occur on ports 22, 80, and 443, which are typically open for secured and plain text communication. Windows Remote Desktop Protocol (RDP) is widely used for remote communication and has a large number of CVEs and patches for remote code execution vulnerabilities. Another serious risk is File Transfer Protocol (FTP). Many devices such as cameras, printers, and uninterruptible power supplies have these ports open. This widget helps organizations reduce potential risk from these ports. Tenable recommends closing ports that are not in use and addressing any vulnerabilities associated with them, in case they are inadvertently re-opened. The requirements for this widget are: Tenable.io Vulnerability Management (Nessus, NNM).
Vulnerabilities on Privileged Ports – This widget provides a count of vulnerabilities by Privileged TCP port (<1024), and severity or exploitability. The TCP/IP port numbers below 1024 are reserved for system use – non-privileged users are not allowed to run services on them. This security feature ensures only authorized services are running. Visualizing risk based on TCP ports help security teams to easily identify risk associated with common attack paths. The requirements for this widget are: Tenable.io Vulnerability Management (Nessus, NNM).
CVSS Vulnerability Counts Per Port – This widget uses CVSSv3 scores to communicate the risk of discovered vulnerabilities. There are seven rows, each one for a CVSS level starting with 10 and ending with 4. Next, there are eight columns with port filters for less than 1024, greater than 1024 and unique filters for FTP, SSH, SMTP, HTTP and HTTPS. The colors used are yellow (medium), orange (high), and red (critical). The requirements for this widget are: Tenable.io Vulnerability Management (Nessus, NNM).
VPR Count Per Port (Explore) – This widget uses Vulnerability Priority Rating (VPR) scores to communicate the risk of discovered vulnerabilities. There are seven rows, each one for a VPR Score starting with 10 and ending with 4. Next, there are eight columns with port filters for less than 1024, greater than 1024 and unique filters for FTP, SSH, SMTP, HTTP and HTTPS. The colors used are yellow (medium), orange (high), and red (critical). The requirements for this widget are: Tenable.io Vulnerability Management (Nessus, NNM).